CompTIA Securtiy+ Set11 A_3_3_IDS_and_SIEM
CompTIA Securtiy+ Set11 A_3_3_IDS_and_SIEM
CompTIA Securtiy+ Set11 A_3_3_IDS_and_SIEM
1007
Which of the following control types are alerts sent from a SIEM fulfilling based on vulnerability signatures?
0797
A security analyst is interested in setting up an IDS to monitor the company network. The analyst has been told
there can be no network downtime to implement the solution, but the IDS must capture all of the network traffic.
Which of the following should be used for the IDS implementation?
0548
An organization wants to implement a solution that allows for automated logical controls for network defense. An
engineer plans to select an appropriate network security component, which automates response actions based on
security threats to the network. Which of the following would be MOST appropriate based on the engineer’s
requirements?
0022
A security analyst is reviewing the following output from an IPS:

Given this output, which of the following can be concluded? (Select two.)
0544
A security analyst receives a notification from the IDS after working hours, indicating a spike in network traffic.
Which of the following BEST describes this type of IDS?
0297
Joe, a website administrator, believes he owns the intellectual property for a company invention and has been
replacing image files on the company's public facing website in the DMZ. Joe is using steganography to hide stolen
data.
Which of the following controls can be implemented to mitigate this type of inside threat?
0997
Joe, a user at a company, clicked an email link that led to a website that infected his workstation. Joe was
connected to thenetwork, and the virus spread to the network shares. The protective measures failed to stop this
virus, and it has continued to evade detection.
Which of the following should a security administrator implement
to protect the environment from this malware?
0928
A network administrator has been asked to install an IDS to improve the security posture of an organization. Which
of the following control types is an IDS?
0746
An organization's research department uses workstations in an air-gapped network. A competitor released
products based on files that originated in the research department. Which of the following should management do
to improve the security and confidentiality of the research files?
0152
After a routine audit, a company discovers that engineering documents have been leaving the network on a
particular port. The company must allow outbound traffic on this port, as it has a legitimate business use. Blocking
the port would cause an outage. Which of the following technology controls should the company implement?
0192
While reviewing the monthly internet usage it is noted that there is a large spike in traffic classified as "unknown"
and does not appear to be within the bounds of the organizations Acceptable Use Policy.
Which of the following tool or technology would work BEST for obtaining more information on this traffic?
0554
A small-to-medium sized company wants to block the use of USB devices on its network. Which of the following is
the MOST cost-effective way for the security analyst to prevent this?
0799
A systems administrator is receiving multiple alerts from the company NIPS. A review of the NIPS logs shows the
following:
reset both: 70.32.200.2:3194 -> 10.4.100.4:80 buffer overflow attempt
reset both: 70.32.200.2:3230 -> 10.4.100.4:80 directory traversal attack
reset client: 70.32.200.2:4019 -> 10.4.100.4:80 Blind SQL injection attack
Which of the following should the systems administrator report back to management?
Hint: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClT9CAK
0419
A security administrator learns that PII, which was gathered by the organization, has been found in an open forum.
As a result, several C-IeveI executives found their identities were compromised, and they were victims of a recent
whaling attack. Which of the following would prevent these problems in the future? (Select TWO).
0434
A technician receives a device with the following anomalies:
- Frequent pop-up ads
- Slow response time switching between active programs
- Unresponsive peripherals
The technician reviews the following log file entries:
File Name Source MD5 Target MD5
Status
antivirus.exe F794F21CD33E4F57890DDEA5CF267ED2 F794F21CD33E4F57890DDEA5CF267ED2 Automatic iexplore.exe 7FAAF21CD33E4F57890DDEA5CF29CCEA AA87F21CD33E4F57890DDEAEE2197333 Automatic service.exe 77FF390CD33E4F57890DDEA5CF28881F 77FF390CD33E4F57890DDEA5CF28881F Manual USB.exe E289F21CD33E4F57890DDEA5CF28EDC0 E289F21CD33E4F57890DDEA5CF28EDC0 Stopped
Based on the above output, which of the following should be reviewed?
0833
The application team within a company is asking the security team to investigate why its application is slow after an upgrade. The source of the team's application is 10.13.136.9, and the destination IP is 10.17.36.5. The security analyst pulls the logs from the endpoint security software but sees nothing is being blocked. The analyst then looks at the UTM firewall logs and sees the following:
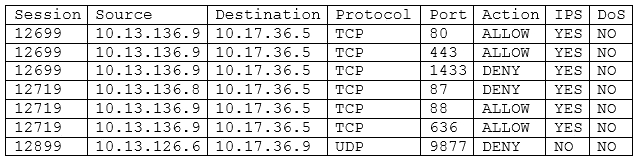
Which of the following should the security analyst request NEXT based on the UTM firewall analysis?
0242
A computer on a company network was infected with a zero-day exploit after an employee accidently opened an
email that contained malicious content. The employee recognized the email as malicious and was attempting to
delete it, but accidently opened it.
Which of the following should be done to prevent this scenario from occurring again in the future?
0487
A security administrator installed a new network scanner that identifies new host systems on the network. Which
of the following did the security administrator install?
0754
A security administrator receives alerts from the perimeter UTM. Upon checking the logs, the administrator finds
the following output:
Time: 12/25 0300
From Zone: Untrust
To Zone: DMZ
Attacker: externalip.com
Victim: 172.16.0.20
To Port: 80
Action: Alert
Severity: Critical
When examining the PCAP associated with the event, the security administrator finds the following information:
<script>alert("Click here for important information regarding your account! http://
externalip.com/account.php");</script>
Which of the following actions should the security administrator take?
0502
A security administrator is trying to eradicate a worm, which is spreading throughout the organization, using an
old remote vulnerability in the SMB protocol. The worm uses Nmap to identify target hosts within the company.
The administrator wants to implement a solution that will eradicate the current worm and any future attacks that
may be using zero-day vulnerabilities. Which of the following would BEST meet the requirements when
implemented?
0053
A security administrator has found a hash in the environment known to belong to malware. The administrator
then finds this file to be in in the pre-update area of the OS, which indicates it was pushed from the central patch
system.
File: winx86_adobe_flash_upgrade.exe
Hash: 99ac28bede43ab869b853ba62c4ea243
The administrator pulls a report from the patch management system with the following output:

Given the above outputs, which of the following MOST likely happened?
0697
A salesperson often uses a USB drive to save and move files from a corporate laptop. The coprorate laptop was
recently updated, and now the files on the USB drive are read-only. Which of the following was recently added to
the laptop?
0405
The Chief Information Security Officer (CISO) is asking for ways to protect against zero-day exploits. The CISO is
concerned that an unrecognized threat could compromise corporate data and result in regulatory fines as well as
poor corporate publicity. The network is mostly flat, with split staff/guest wireless functionality. Which of the
following equipment MUST be deployed to guard against unknown threats?
0991
A company is having issues with intellectual property being sent to a competitor from its system. The information
being sent is not random but has an identifiable pattern.
Which of the following should be implemented in the system to stop the content from being sent?
0633
A member of the human resources department received the following email message after sending an email
containing benefit and tax information to a candidate:
"Your message has been quarantined for the following policy violation: external potential_PII. Please contact the IT
security administrator for further details".
Which of the following BEST describes why this message was received?
0910
A Security analyst has received an alert about Pll being sent via email. The analyst's Chief Information Security
Officer (CISO) has made it clear that Pll must be handled with extreme care. From which of the following did the
alert MOST likely originate?
0825
An organization plans to transition the intrusion detection and prevention techniques on a critical subnet to an
anomaly-based system.
Which of the following does the organization need to determine for this to be successful?
0955
After patching computers with the latest application security patches/updates, users are unable to open certain
applications. Which of the following will correct the issue?
0762
A company recently implemented a new security system. In the course of configuration, the security administrator
adds the following entry:
#Whitelist USB\VID_13FE&PID_4127&REV_0100
Which of the following security technologies is MOST likely being configured?
0995
An organization is struggling to differentiate threats from normal traffic and access to systems. A security engineer
has been asked to recommend a system that will aggregate data and provide metrics that will assist in identifying
malicious actors or other anomalous activity throughout the environment.
Which of the following solutions should the engineer recommend
0547
A company recently experienced data exfiltration via the corporate network. In response to the breach, a security
analyst recommends deploying an out-of-band IDS solution. The analyst says the solution can be implemented
without purchasing any additional network hardware. Which of the following solutions will be used to deploy the
IDS?
0174
The security administrator receives an email on a non-company account from a coworker stating that some
reports are not exporting correctly. Attached to the email was an example report file with several customer’s
names and credit card numbers with the PIN.
Which of the following is the BEST technical controls that will help mitigate this risk of disclosing sensitive data?
0271
A security administrator needs to implement a system that detects possible intrusions based upon a vendor
provided list.
Which of the following BEST describes this type of IDS?
0406
An organization has several production-critical SCADA1 supervisory systems that cannot follow the normal 30-day
patching policy. Which of the following BEST maximizes the protection of these systems from malicious software?
0927
A company has drafted an Insider-threat policy that prohibits the use of external storage devices. Which of the
following would BEST protect the company from data exfiltration via removable media?
0326
A security administrator suspects that data on a server has been exfiltrated as a result of unauthorized remote
access.
Which of the following would assist the administrator in confirming the suspicions? (Select TWO)
0969
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks.
Which of the following methods would BEST prevent the exfiltration of data? (Select TWO).
0344
An administrator thinks the UNIX systems may be compromised, but a review of system log files provides no useful
information. After discussing the situation with the security team, the administrator suspects that the attacker
may be altering the log files and removing evidence of intrusion activity.
Which of the following actions will help detect attacker attempts to further alter log files?
1010
An analyst has determined that a server was not patched and an external actor exfiltrated data on port 139.
Which of the following sources should the analyst review to BEST ascertain how the incident could have been prevented?